What is BurpSuite Proxy?
BurpSuite - proxy is the core of Burp's operation, which allows you to intercept HTTP traffic and modify the request or response in real-time. Let's look at an example here, i.e., start by launching BurpSuite and moving to the Proxy tool.
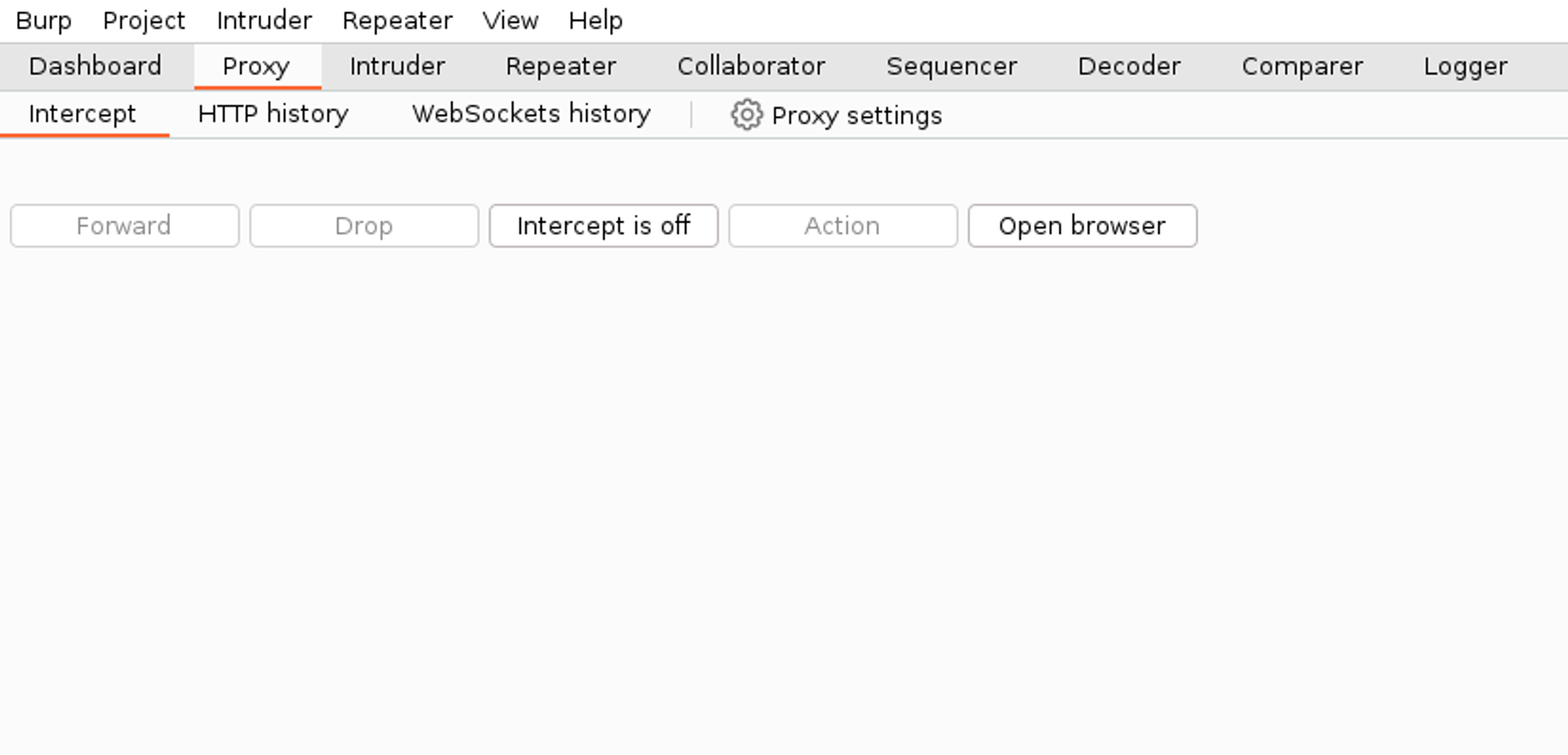
The latest versions of Burp now include a built-in browser that is pre-configured to route traffic through Burp. If you wish to use a different browser, such as Firefox, you can find instructions for this configuration here.
Stopping incoming HTTP traffic
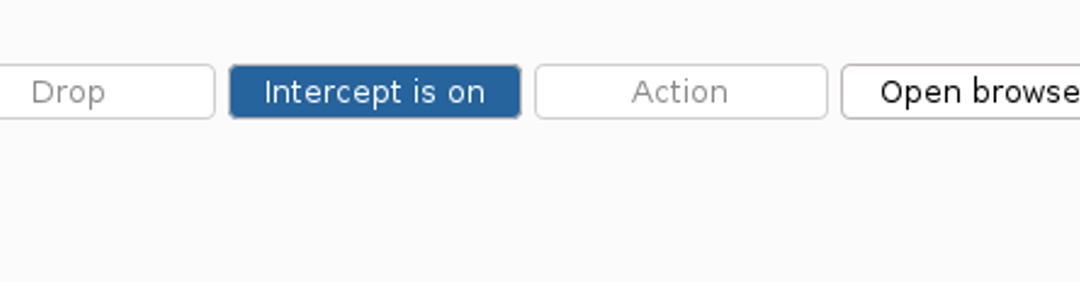
Continue by opening the browser from the Open Browser button. A new browser window should open for you. Next, let's set Burp in a state where it intercepts the traffic between the browser and the application. Otherwise, Burp only saves and forwards that traffic. Click the Intercept is off button to enable the interception function.
Now go to the browser and navigate to the address https://hakatemia.fi/. From here, the HTTP request should now be visible in the Burp Suite tool. Because Burp is set to Intercept mode, it now intercepts every HTTP request and response.
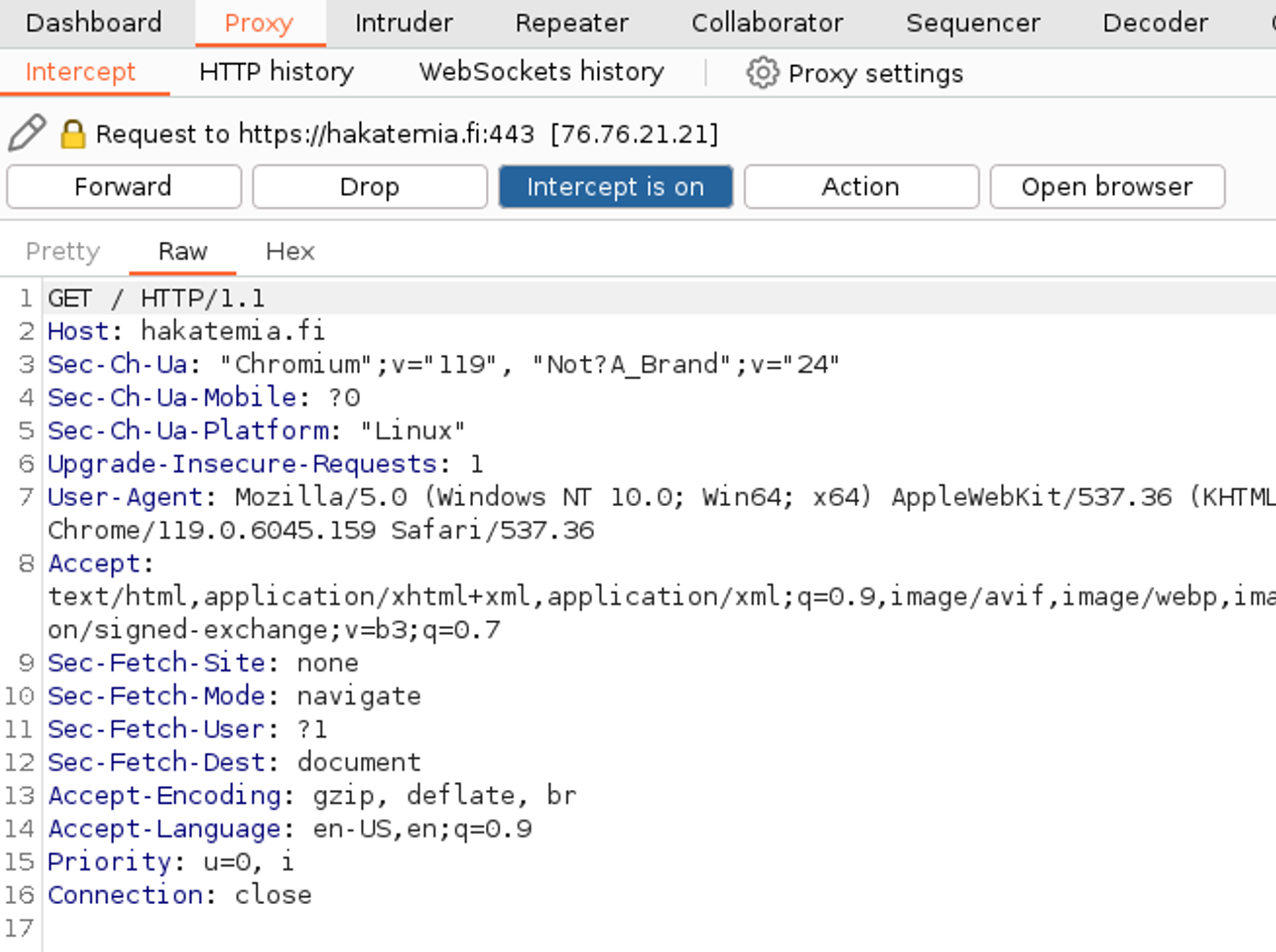
Now we can manipulate the HTTP request or send it to different tools for processing. Let's continue in this example by pressing the Forward button, which forwards the request to the application. It is important to understand that at this stage, the application is not yet aware of the HTTP request in any way. The HTTP request has been sent from the browser and arrived at the Burp tool. When you press the Forward button, Burp sends the request to the application.
Viewing HTTP history
Next, the browser will start fetching and loading the web page resources. This will generate HTTP traffic, which will be visible next in Burp. This is completely normal behavior, but this traffic can often be quite significant, and we do not want to spend our time forwarding each HTTP request separately. Therefore, we can disable interception functionality and let Burp automatically forward this traffic. You can do this by clicking the blue Intercept is on button.
Next, let's navigate to the HTTP history page to view the HTTP history.
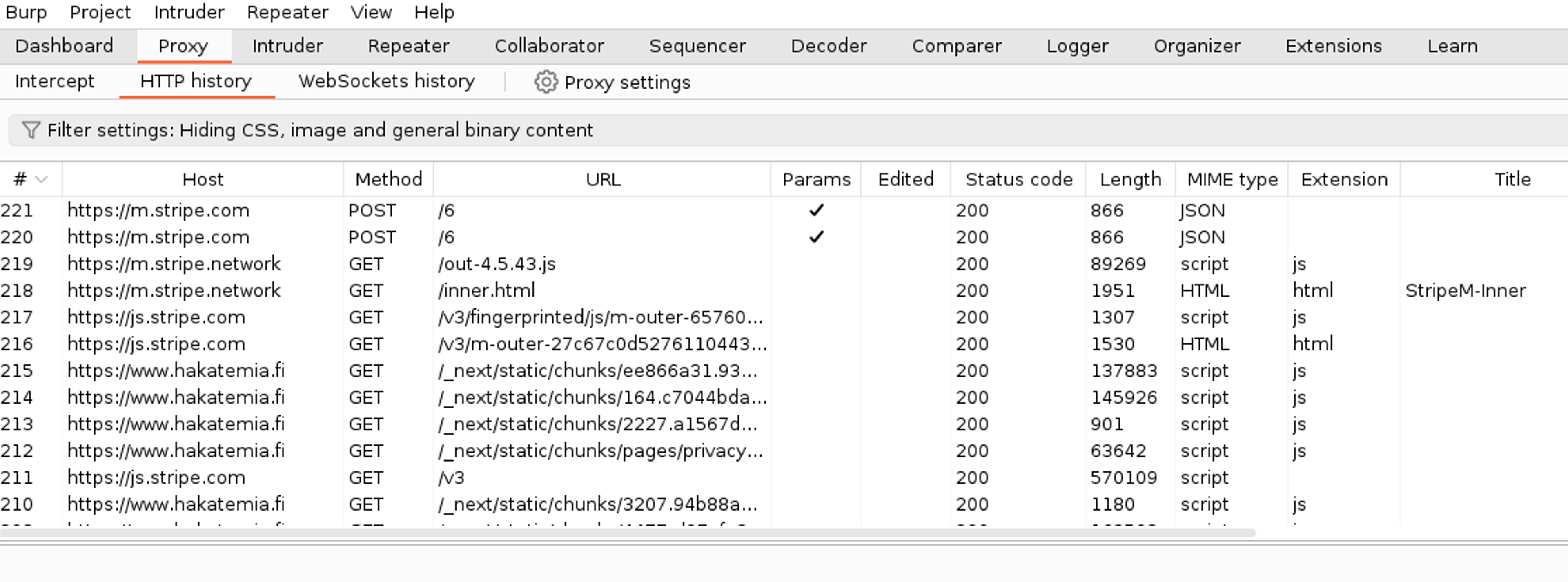
Browse to the beginning of HTTP history and open the first occurred HTTP conversation. This will show you the occurred HTTP request and the HTTP response returned by the application. In this case, the application returned a redirection, i.e. a 308 response, because we navigated to the address https://hakatemia.fi while Hakatemia itself is located at the address https://www.hakatemia.fi. The application handles this correction invisibly, and the user does not notice it.
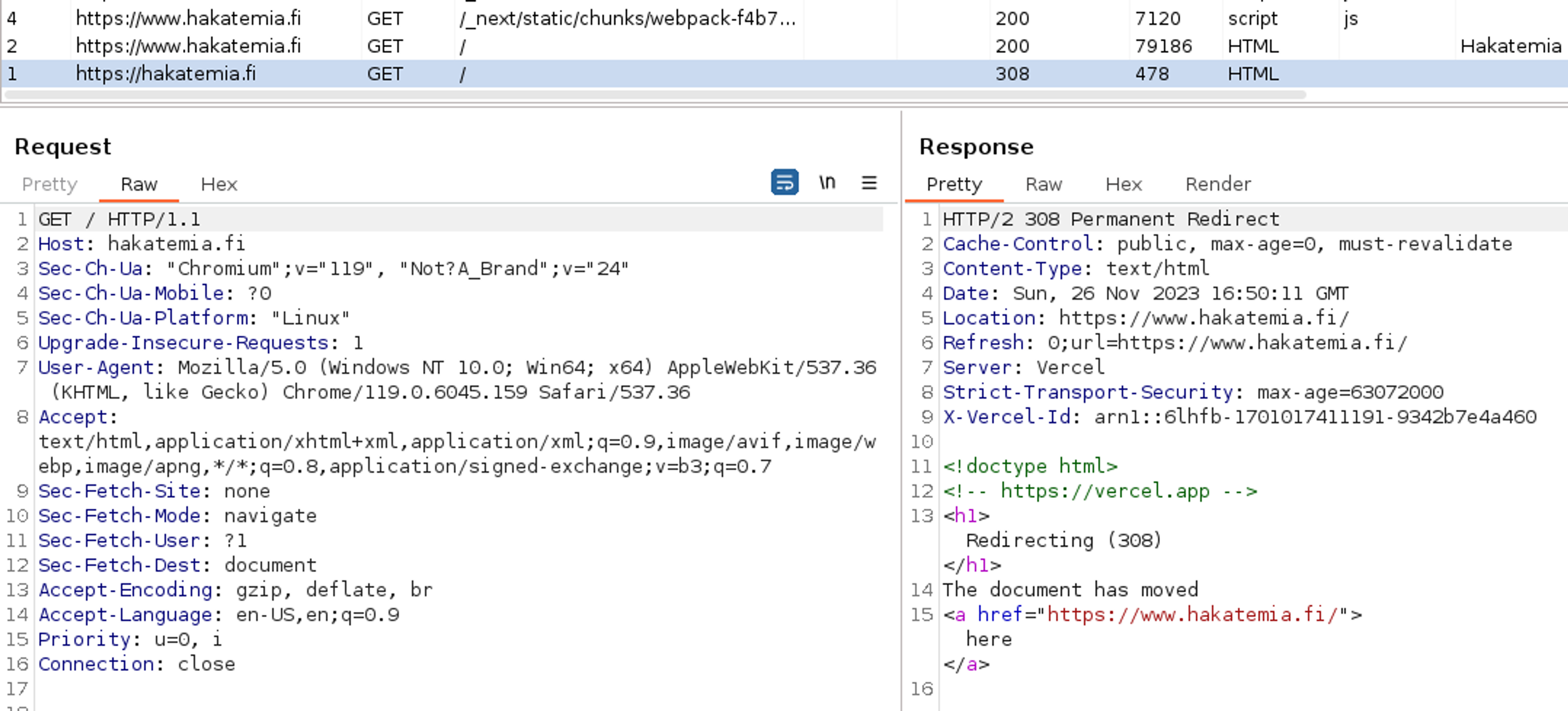
WebSocket History
Let's continue by moving to the WebSockets history page. This page will show you all the stored Web Socket traffic. You can trigger this type of traffic, for example, by navigating to the page https://websocketstest.com/.
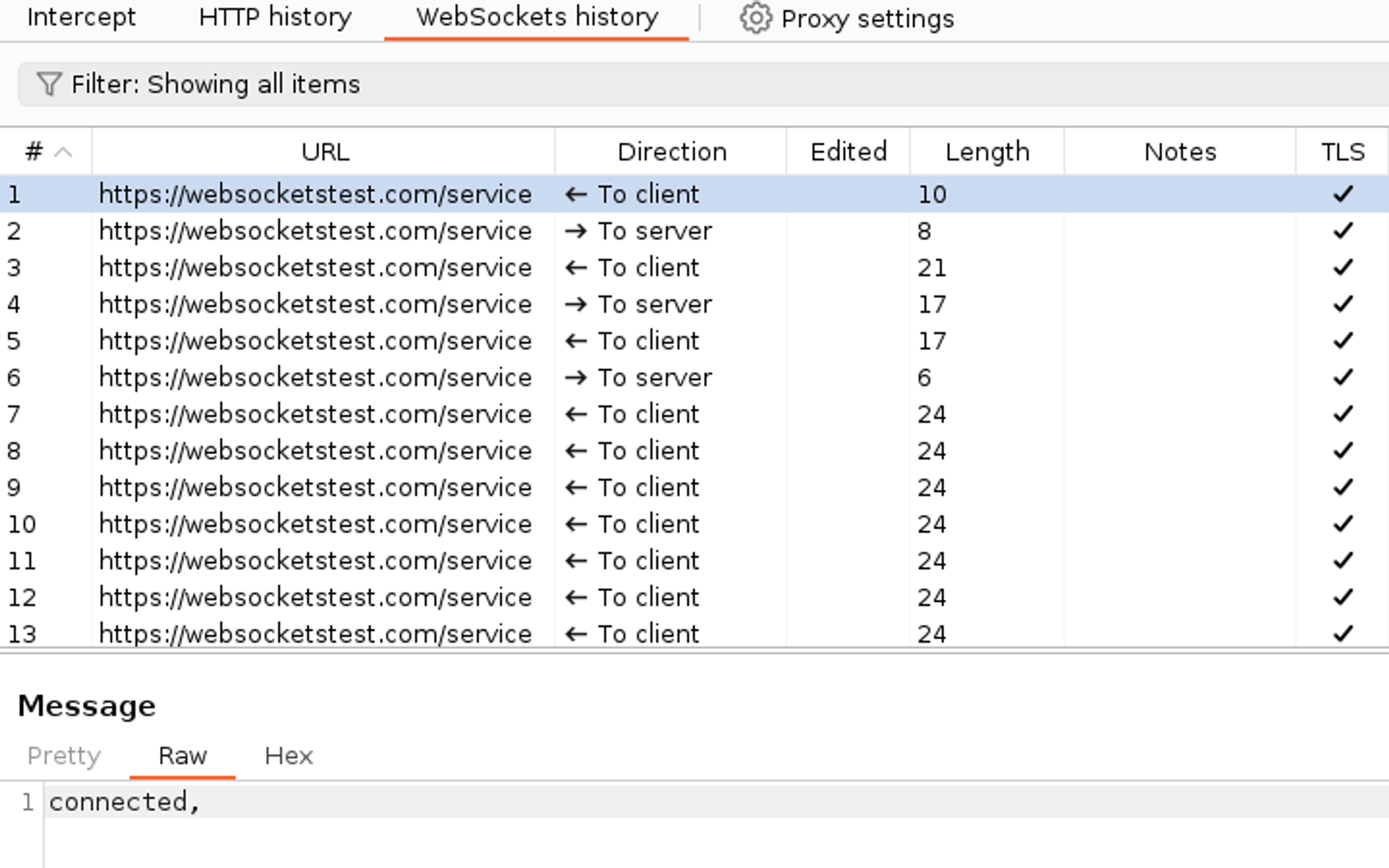
Test your knowledge


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



