Auditing SSH configuration is important, as outdated or vulnerable cryptographic settings can expose systems to security risks. Let's take a look at the different settings that can be configured for the SSH service and how the Nmap ssh2-enum-algos script can be used to audit SSH crypto settings.
SSH and its cryptographic settings
SSH (Secure Shell) is a protocol that provides a secure way to establish an encrypted connection to remote systems. It is widely used among system administrators and cybersecurity experts for remote connections, file transfers, and executing remote commands on servers. The security of SSH is based on its cryptographic settings, which define how encryption and authentication are performed. These settings are audited to ensure that the connection is secured according to current best practices.
Cryptography algorithms (Ciphers)
Encryption algorithms are crucial for the security of SSH connections, as they define how data is encrypted during the connection. Modern algorithms, such as AES (Advanced Encryption Standard) with different key lengths (for example AES-128, AES-192, AES-256) and ChaCha20, provide strong protection. Older algorithms, such as DES and 3DES, are vulnerable and their use should be avoided.
MAC algorithms (Message Authentication Codes)
MAC algorithms are important for ensuring the integrity and authenticity of data. They produce a digest of the message that ensures that the data has not changed during transmission from sender to receiver. Recommended MAC algorithms include hmac-sha2-256 and hmac-sha2-512, while deprecated algorithms such as hmac-md5 and hmac-sha1 should be avoided due to their weaknesses.
Key Exchange Algorithms
Key exchange algorithms define how a shared encryption key is securely created between parties at the beginning of a connection. Diffie-Hellman group and its variants, such as ECDH (elliptic curve Diffie-Hellman) and Curve25519, are popular choices because they provide strong protection. Older or weaker key exchange algorithms, such as diffie-hellman-group1-sha1, are vulnerable to attacks and their use should be avoided.
What is Nmap?
Nmap (Network Mapper) is a free and open-source tool for exploring networks and conducting cybersecurity audits. It enables scanning of network ports, discovery of hosts, and identification of various services. Nmap also provides a wide range of scripts (Nmap Scripting Engine, NSE) that can be used to perform various security checks.
ssh2-enum-algos Script
The Nmap ssh2-enum-algos script is designed to identify which cryptographic algorithms the SSH server supports. This includes encryption techniques (ciphers), message authentication codes (MACs), and key exchange algorithms. The script can be used to identify potentially weak or outdated algorithms that may expose the connection to security threats.
Running the Script
Running the script requires installing Nmap. Once Nmap is installed, you can run the ssh2-enum-algos script from the command line as follows:
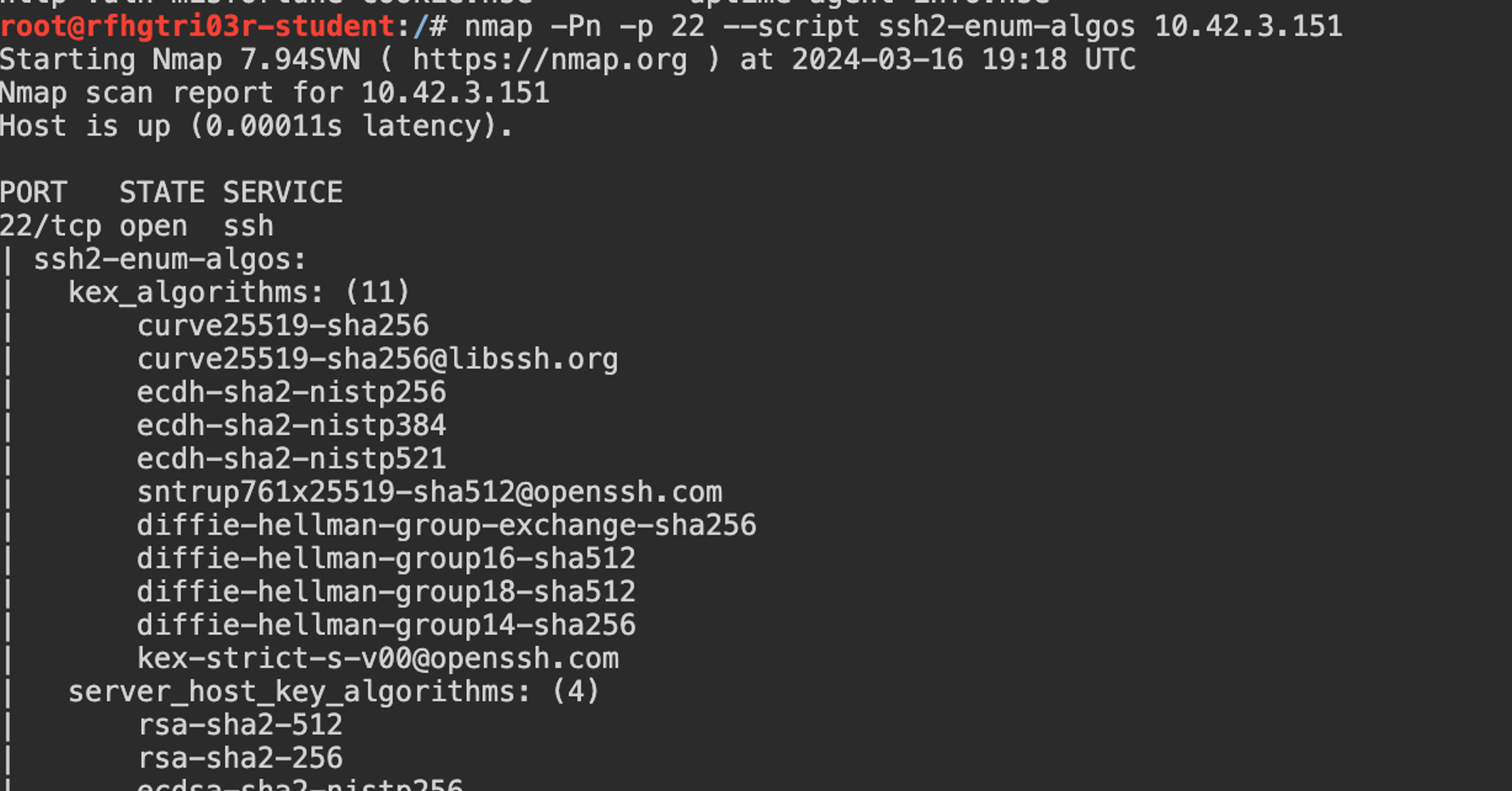
In this command -p 22 defines the port being scanned (SSH default port is 22) and <target IP address> is the IP address of the server selected for auditing.
Interpretation of Results
After running the script, you will receive results that list the supported algorithms. Pay special attention to the following:
- Old Encryption Algorithms: Such as DES, 3DES, or RC4, which are known to be weak.
- Weak MAC algorithms: Such as MD5 or SHA1, which are vulnerable to certain types of attacks.
- Weak key exchange algorithms: Such as diffie-hellman-group1-sha1 using a 1024-bit key. It is considered insecure because it has been shown to be susceptible to certain attacks, such as the Logjam attack. Weaknesses in the SHA-1 hash function increase its vulnerability.
Exercise
Start the task below. Check the IP address of the target from the "Internal network targets" section.
Next, run the nmap ssh2-enum-algos script on the target.
Which of the supported MAC algorithms is the weakest?


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



