In this module, we will go through how you can install antivirus software in a Linux environment. Often, it is thought that a Linux environment does not need antivirus because most malware is designed to target Windows environments, and this is mostly true. However, there are many situations where it is useful to use antivirus on a Linux server as well. For example, if you have a critical system that must operate without issues, antivirus software can be a good idea to ensure that no malicious software infects it. And if something does manage to get in, it can be quickly caught and dealt with.
Start the laboratory below and follow the steps. In this task, installations and other actions are performed on the local kali machine, not on the target server.
Installation
First, let's go through how to install antivirus software and then practice using it. Then, let's write a simple script to monitor desired folders.
ClamAV installation and updating the virus database
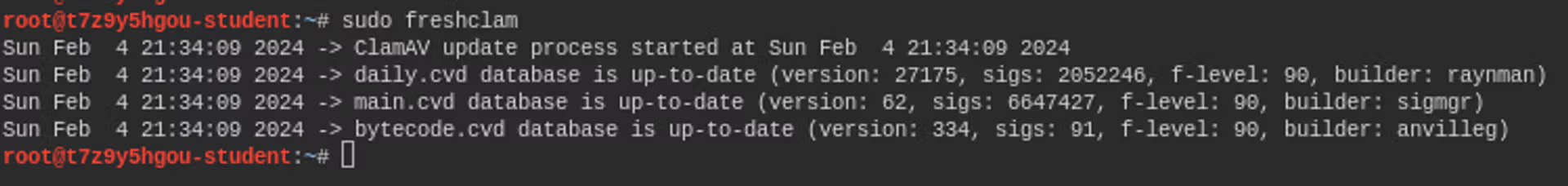
To install the ClamAV software, you can execute the commands below.
apt-get install clamav clamav-daemon
freshclamThe command freshclam downloads the latest virus databases, which allows ClamAV to distinguish malware from regular programs. Typically, this command would be set to run automatically, perhaps once a day, to ensure that the latest virus signatures are always available.
Usage
Scan a specific file or directory
clamscan /path/file-or-directoryThis command scans either a single file or a directory, but not subdirectories within the folder. It is not recursive.
Scan the entire system (requires administrator rights)
sudo clamscan -r /This scans the whole operating system, so it is recursive.
Scan and display all files detected with infections
clamscan -r --bell -i /This scans the entire system and displays a beep sound (--bell) and outputs the detected infections (-i).
Move infected files to quarantine
sudo clamscan -r --move=/path/to/quarantine /path/to/scanThis scans the given path (/path/to/scan) and moves the detected infected files to quarantine (/path/to/quarantine).
Automating Clamscan with a Script
Next, we will write a simple script that scans our home directory every 2 minutes. This script will also move any detected malicious files to their own folder.
The script looks like this. Remember to create folders /viruses, where all detected harmful files will be moved to, and /logs where the scanning logs will be moved to.
#!/bin/bash
while true
do
clamscan -r --log=/logs/$(date +"%y-%m-%d-%H-%M-%S").log --move=/viruses /root/
sleep 120
doneLet's run a script in the background and save a test virus in the home directory. For the sake of convenience, it is advisable to run the screen program and run the script in a screen session.
Run the command screen and execute the script inside it.
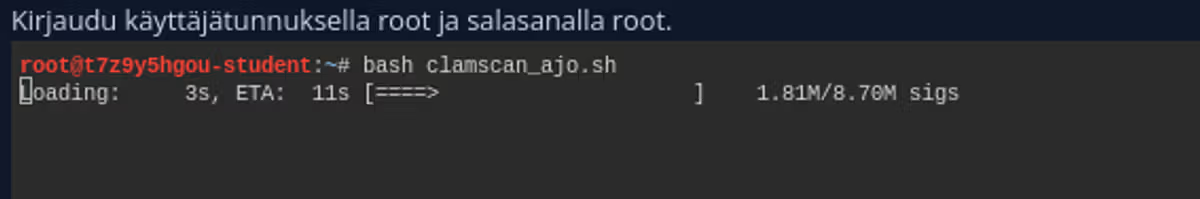
Now our script performs scans every two minutes. You can jump out of the screen program and leave this running by pressing Ctrl-a + d.
Testing the trial virus (eicar.txt)
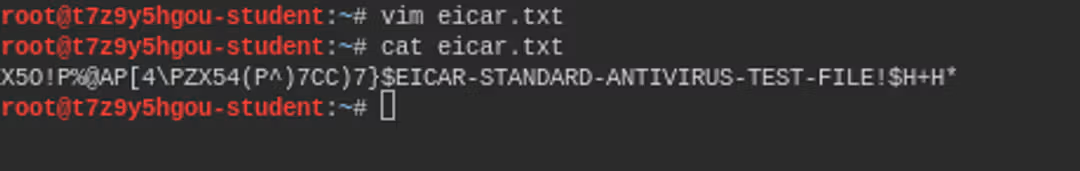
Save a file named eicar.txt to the home directory and insert the following string into it. This is a test file that triggers antivirus software alerts but is not dangerous in any way.
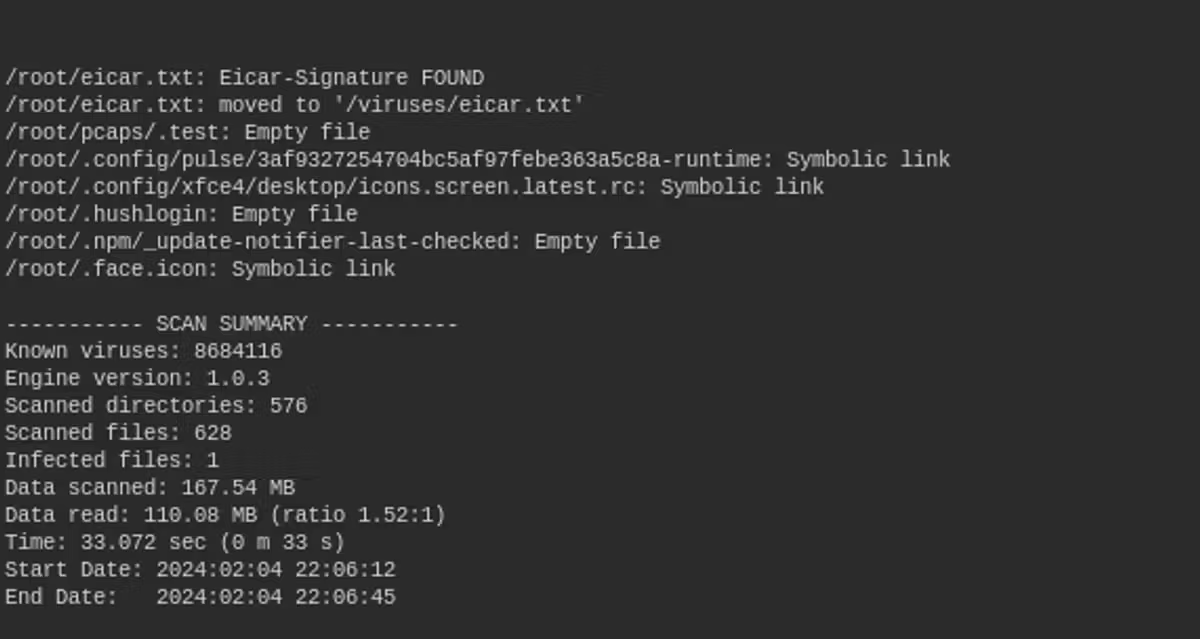
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*And we notice how the antivirus detects our file and processes it in the desired way, moving it to the desired location.

Log file caused by a test virus.
Questions
Which of the following commands is incorrect?


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



