In this module, we will practice configuring firewall rules in the Linux world. Start the lab below and repeat the steps afterwards.
Theory
Firewall management in a Debian environment often happens using the iptables tool or at a higher level, the ufw (Uncomplicated Firewall) tool. Let's first take a look at what these are.
iptables
iptables is a tool designed for managing firewalls in the Linux kernel. It provides precise control over how network traffic is filtered, directed, and includes packet NAT handling.
General concepts:
- Chains: iptables uses concepts called "chains" that define what happens to a specific type of traffic.
- Rules: Each chain consists of rules that determine how traffic is processed.
Example:
# Block all incoming connections from non-local traffic
sudo iptables -P INPUT DROP
# Allow all outgoing connections
sudo iptables -P OUTPUT ACCEPT
# Allow traffic in local traffic
sudo iptables -A INPUT -i lo -j ACCEPTThis is just a simple example. iptables rules can be more complex depending on the needs, and they can be configured in many different ways.
ufw (Uncomplicated Firewall)
ufw is a simple interface for iptables, making firewall management easier. It is often installed on Debian systems and can facilitate basic firewall management.
Example:
Ufw contains ready-made rules for known services, such as SSH, and makes it easier to add new rules.
Exercise
Perform the following exercise, in which we first install the ufw tool and then define clear firewall configurations with it. Start the laboratory below and repeat the steps afterwards.
Installing ufw tool
Let's start by installing the ufw tool. Connect to the target server and run the following command.
sudo apt update && sudo apt install ufw -yBlock all inbound traffic ports except SSH and HTTP(S)
Execute the following commands on the target server.
sudo ufw allow ssh
sudo ufw allow 80/tcp
sudo ufw allow 443/tcp
sudo ufw default deny incoming
sudo ufw default allow outgoing
sudo ufw enableFirst, allow the desired ports, namely SSH, HTTP, and HTTPS. Then make sure that all incoming traffic is blocked by default (except for allowed ones) and allow all outgoing traffic. Finally, enable the firewall. Note! - Currently, the lab environment does not support this usage, so there is no need to worry about error messages. Unfortunately, at the moment, you cannot verify the functionality of the firewall in practice.
You can view the rules by running the command:
sudo ufw show addedIf everything has been done correctly, the output should appear as follows.
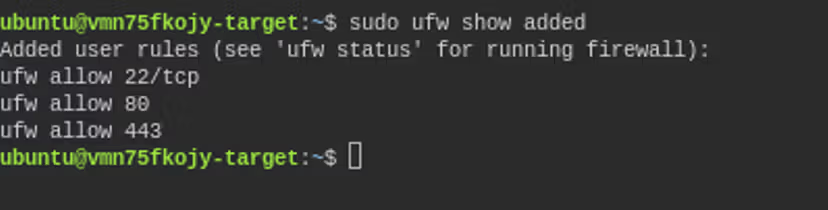
Which ports are allowed in the configuration below?
ufw allow 80/tcp
ufw allow 443/tcp
ufw allow 4444
ufw allow 22/tcpAnswer correctly


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



