What is SSH?
SSH (Secure Shell) is software that uses encrypted protocol and allows for secure remote connection between computers over the Internet. The main purpose of SSH is to provide encrypted and secure access to remote servers and devices. It is typically used to manage remote servers, securely transfer files, and execute commands on remote machines. In this module, we will learn how to use SSH. Start by running the exercise below and follow the steps at your own pace.
Establishing SSH connection
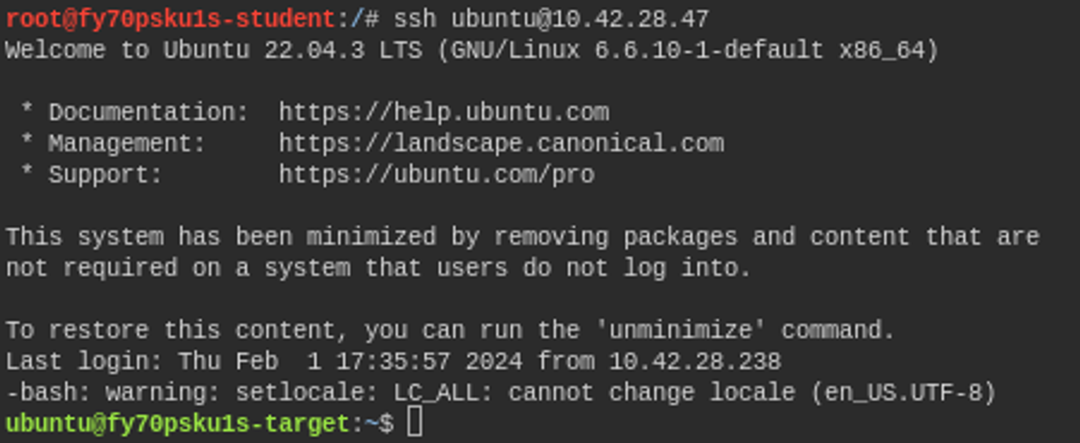
Using the SSH program is relatively straightforward. Once your exercise lab has started, you can connect to the target IP address with the following command:
ssh ubuntu@TARGET-IPThe above command contains the word ubuntu, which is the user we want to log in as. Then comes the @ symbol, after which we give the IP address or domain name we want to connect to. After this, the service confirms that you want to create a connection to this destination, as the fingerprint of the destination is not recognized. You can only press yes. Finally, the service asks for the user's password. The password is hakatemia.
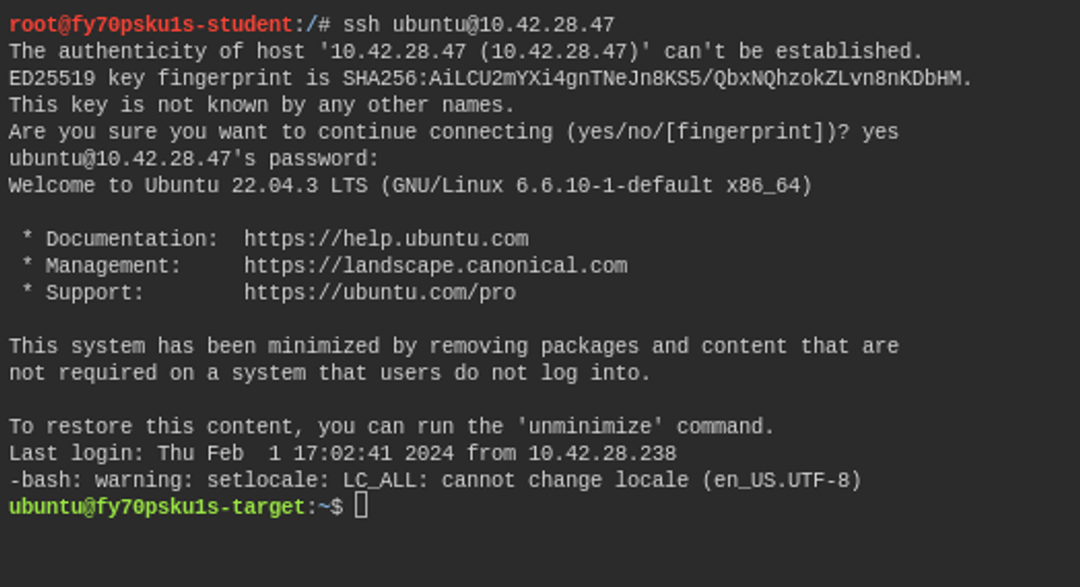
Now we are logged in remotely to the target machine as user ubuntu.
Creating and using a public SSH key
The SSH service supports several different ways to authenticate access to servers. We just used the traditional password login, but there is a safer and better way, namely using SSH keys. SSH keys are based on asymmetric cryptography and the logic behind it is as follows:
- Key generation: Initially, the user generates a key pair. This consists of a public key that is shared with servers, and a private key that is securely kept on the user's own device.
- Establishing Connection: When a user contacts, the server wants to ensure the user's identity. It asks the user to sign a random challenge with their private key.
- Signature verification: The receiving party verifies that the received signature matches the expected one by using its public key. If it is correct, the user's identity is confirmed.
There is no need to enter a password every time a connection is established when using SSH keys, which makes the process more convenient. Only with the private key can access be granted to selected services, so it must be well protected.
You can generate an SSH key pair for yourself with the following command (remember to run this on your own machine, not the target machine):
ssh keygenThe command first asks you where you want to save the key pair, and then if you want to set a password for the private key. This way it cannot be used without knowing the password, which adds this protection. You can just press enter if you do not want to set a password for it.
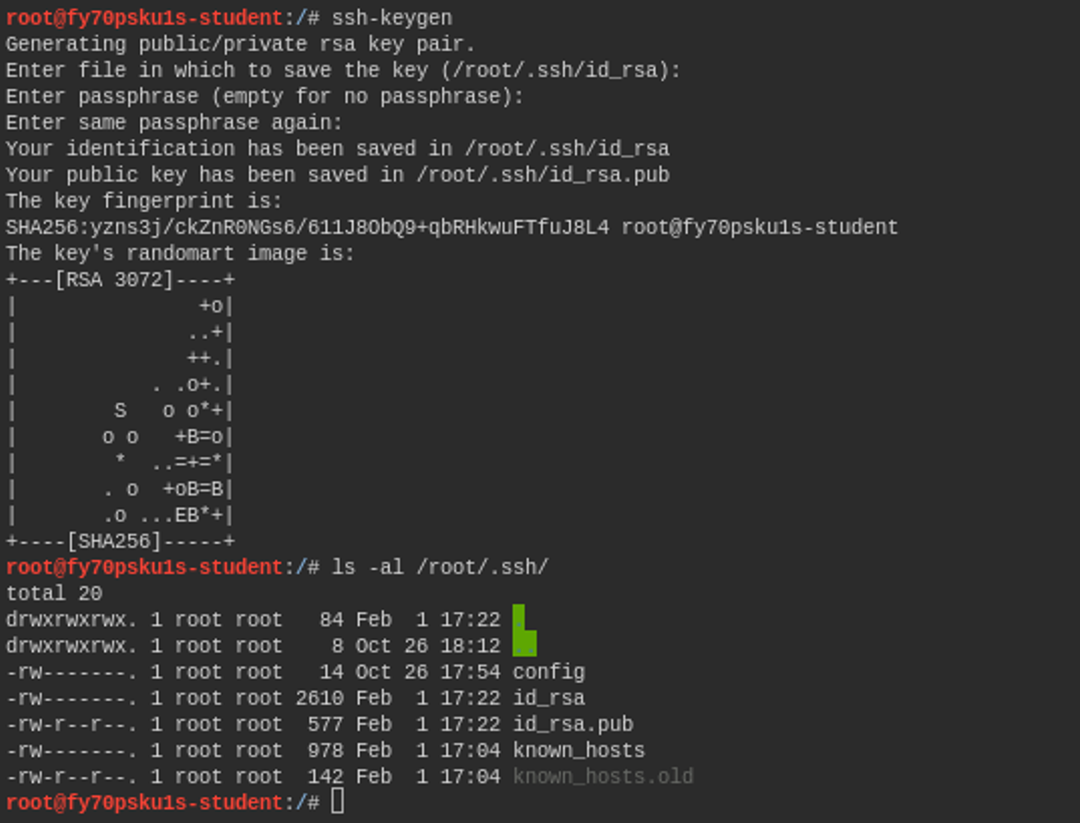
In the above list, the files id_rsa and id_rsa.pub are the keys that were just generated. The one with the .pub extension is your public key, which you can freely distribute to the target servers where you want to log in via SSH connection.
Setting the Public Key for the Target Server
The next step is to set the respective public key to the target server so that we can log in using it. At the same time, let's practice how you can transfer files from one server to another over SSH protocol. We will use a command called SCP in the following way:
scp FROM WHERE TO WHAT
# for example, a target from a machine to our machine
scp ubuntu@10.0.0.1:"/tama" /root/tanne
# Or from our machine to the target machine
scp /root/.ssh/id_rsa.pub ubuntu@10.0.0.1:"/"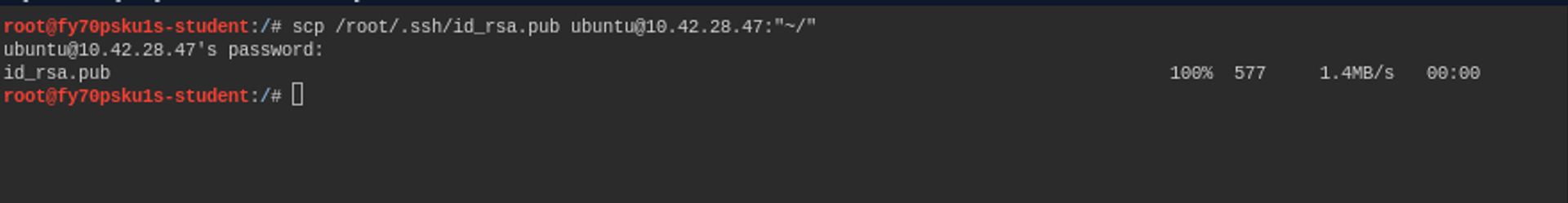
The command asks you for a password and then transfers the file to the target machine. Now we log in to the destination machine with SSH as usual and set the public SSH key correctly.
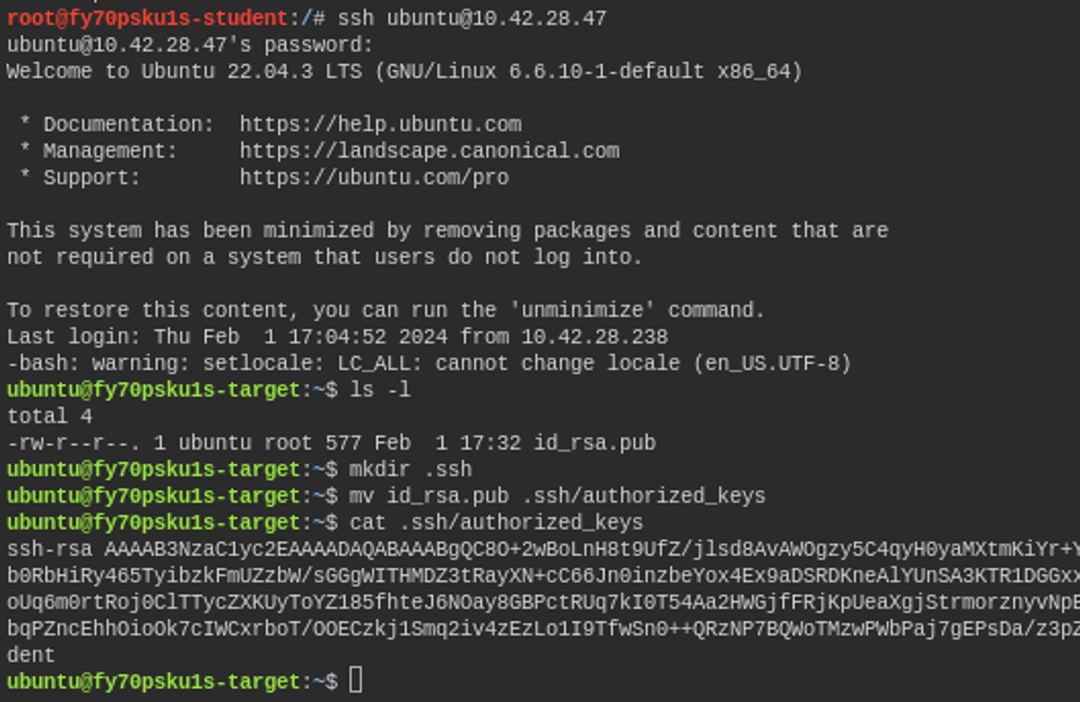
When attempting to log in to an SSH service using public keys, the service will verify whether the user (the user you are trying to log in as) has a file called .ssh/authorized_keys in their home directory.
The file in question contains all the specified public keys, and there can be multiple of them, each on its own line. In the image above, we simply created a folder named .ssh in the user's home directory and moved the recent id_rsa.pub file inside this folder.
We also changed the name of this to match that authorized_keys name. (Note! - This is not a good example of how to do this, as it would have been more sensible to just copy the public key instead of transferring the entire file, but we also went through that SCP command here.)
Now we can try to log in again and notice that the service no longer asks us for a password. The service uses recently generated SSH keys for authentication.
If you would remove your private key, then the service would resort to password authentication again.
Password login vs. SSH key usage
Keys provide a higher level of security, as they are long and random strings, unlike typical passwords. Secondly, keys can be used without the user having to enter a password every time. This makes the process more convenient and reduces the risk of users using weak passwords or storing them in insecure locations. In addition, keys enable automated processes and, for example, scripts can safely use keys without the user having to be present and enter a password. Overall, SSH keys provide an efficient and secure way to authenticate users and protect remote connections.
Which of the following commands does not work?


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



