In this module, we will go through how to open GUI-based applications such as a browser over an SSH tunnel. We will also cover how to create tunnels to other target servers through SSH for ports that may not be directly open to us.
Let's start by launching the exercise task below and repeating the steps below.
Using X11 Forwarding
When enabling X11 Forwarding via SSH, you can run graphical applications on a remote server, but their user interface is displayed and controlled locally. This allows, for example, the use of programs that require a graphical user interface, such as text editors, image processing programs, or graphical applications.
Checking X11 Forwarding Configuration
In order to use X11 Forwarding, it must be enabled in the SSH service. Let's check this by logging into the server via SSH and opening the SSH configuration file with the 'nano' program.
SSH service configuration file can be found at path /etc/ssh/sshd_config.
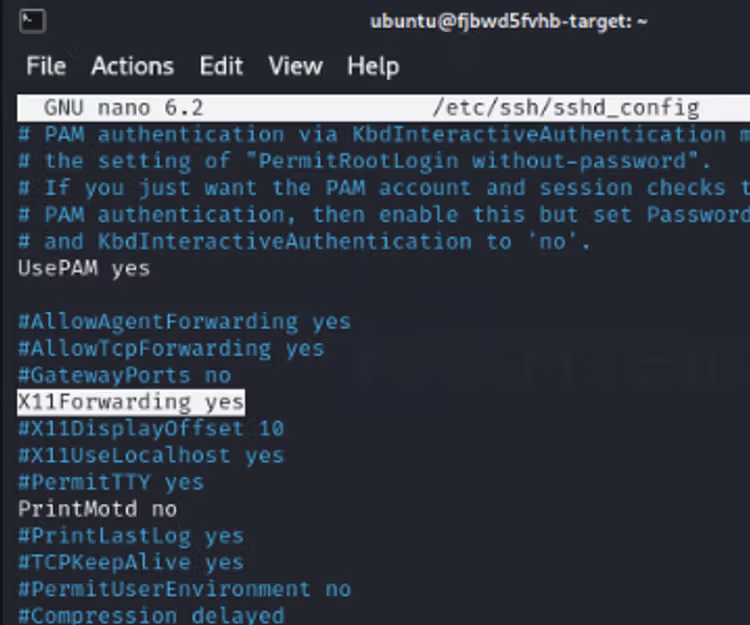
Using X11 Forwading
Now that we know that this is enabled and supported, we can try to launch the nautilus program so that its interface opens on our Kali machine even though the process itself is running on a remote machine.
In order for the user interface to be carried through an SSH tunnel, you must create an SSH connection using the -X flag, as shown in the example below. After that, you can simply launch the nautilus program by typing the command nautilus.
ssh -X ubuntu@10.0.0.1
SSH port forwarding
What does SSH port forwarding mean?
SSH Port Forwarding, also known as SSH tunneling, is a technique that allows traffic to be routed securely over an SSH connection from a specific port or protocol. This is useful when securely transferring traffic between two different devices or accessing servers and resources that are not directly accessible over the Internet.
SSH Port Forwarding can be divided into three main types:
Local Port Forwarding:
- Used to connect a local machine to another server or port via a remote server.
- For example, you can use a local port on a specific machine and redirect the traffic through a remote machine to another machine.
ssh -L local_port:remote_server:remote_port user@remote_serverRemote Port Forwarding:
- Used to turn a remote machine into a port listener on a local machine.
- You can make a locally available service accessible through a remote machine.
ssh -R remote_port:local_machine:local_port user@remote_serverDynamic Port Forwarding (Dynamic SOCKS Proxy):
- Create a dynamic proxy server that allows routing of multiple traffic through an SSH connection.
- Typically used for secure browsing on open Wi-Fi networks.
ssh -D local_socks_port user@remote_serverSSH Port Forwarding allows you to secure your traffic using an encrypted SSH connection and access services that are not directly accessible through the internet. It is an effective way to secure the connection and enable reliable resource usage.
SSH port forwarding example
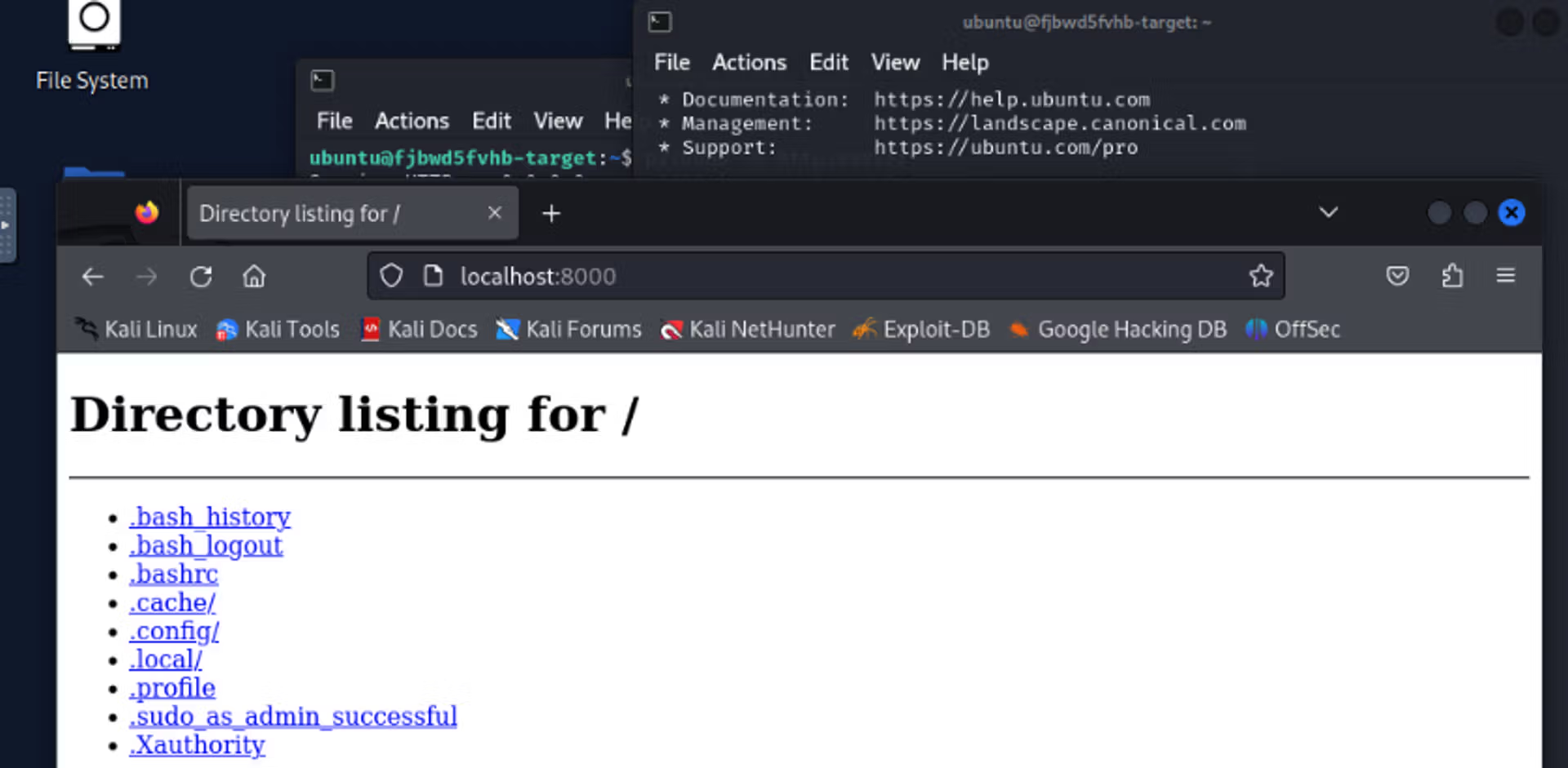
Next, we will set up a simple HTTP service on a remote machine, allowing access only locally on port 8000. Then, we will establish an SSH tunnel to browse the same HTTP service using our own browser in Kali.
Setting up an HTTP server on a remote machine
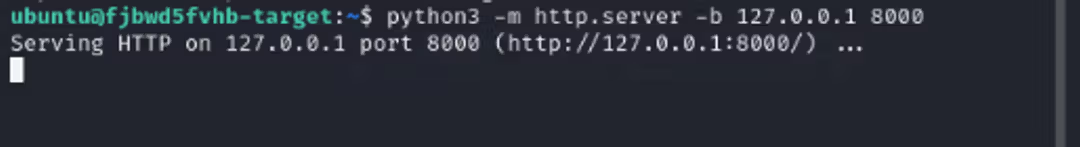
Execute the command in the image and open a new terminal. Now there is an HTTP service running on port 8000 locally on the remote machine, so we cannot access the service without SSH tunneling. This requires local port forwarding.
Creating SSH tunnel
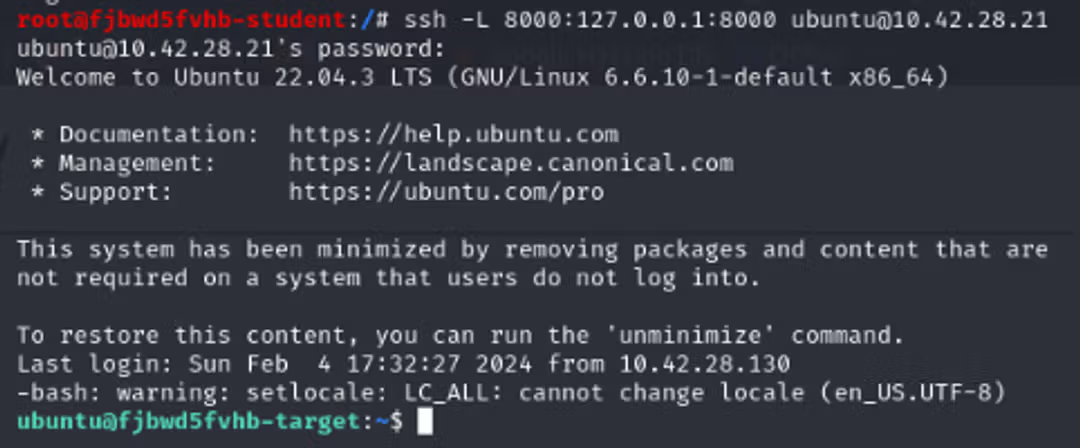
The command "vipu -L" refers to local port forwarding, and the first port specifies which port is reserved on our machine. After that, we determine to which IP address and port the tunnel is built on the remote machine.
Navigation to HTTP service
After this, the browser can be opened and navigate to the local port 8000 of the Kali machine, through which the traffic flows through the SSH tunnel to the remote machine's port 8000, where the HTTP service is running.
Type the command that you can use to create a local port forwarding through the remote machine of the tunnel to the address 6.6.6.6 on port 4444. On my machine, port 7000 is used. The IP of the remote machine is 10.0.0.1 and the username is ubuntu.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



