What are templates?
Old-fashioned web applications built (and partly still build) HTML responses like this.
html = "<h1> Welcome, " + name + "</h1> return htmlThis type of HTML structure is not only rigid but also terribly insecure. Such applications are usually quite easy to inject the attacker's own HTML/JavaScript code, which leads to XSS vulnerabilities.
A more modern approach is to use templates. Templates are separate HTML files that are also partly code files. The desired data is then given to the template, and the template builds the HTML. There is no vulnerability in this code because the template can safely build the HTML in a way that it doesn't matter what the attacker has entered as a name, it doesn't become dangerously part of the HTML structure.
template = "<h1> Welcome, {{name}}</h1> " return render_template(template, name=name)Template Injection
Template injection vulnerability is very similar to traditional HTML injection (which leads to XSS vulnerability), but much more serious because unlike HTML (which is executed in the browser), templates are executed as code on the server side before the resulting HTML built as a result of template execution is returned to the browser.
This is an example of a vulnerable Flask application that incorrectly uses the Jinja2 template engine, allowing user input to affect the template itself, rather than just the data given to the template, as it should have been.
if request.method == 'POST': name = request.form['name'] template = f'<h1> Welcome, { name }!</h1> ' return render_template_string(template) else: template = '''<form method="POST"> <label for="name">Name:</label><input type="text" name="name" id="name"> <button type="submit">send</button></form> ''' return render_template_string(template)Detecting Vulnerabilities
Python's JInja2 is not the only template engine, but there are many of them for different programming languages. However, almost all template engines share the syntax where double curly braces execute an expression, such as printing a variable or performing a calculation.
The traditional way to detect template injections is to input {{7*7}} in the input and check if the application returns "49" in the same place in the HTML. This is a clear indication of a template injection.
Let's try:
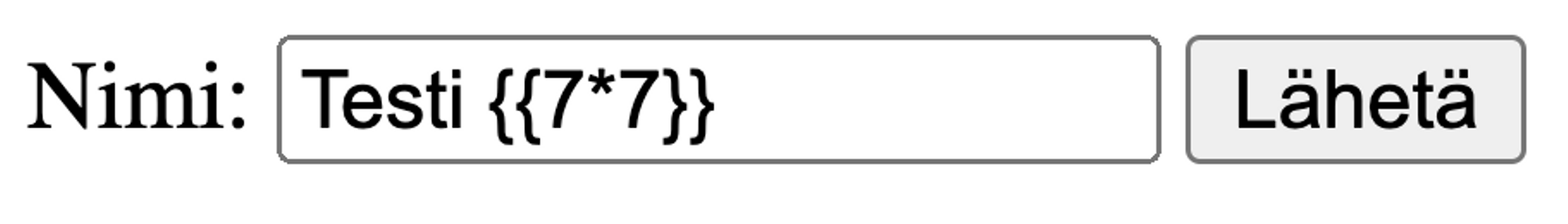
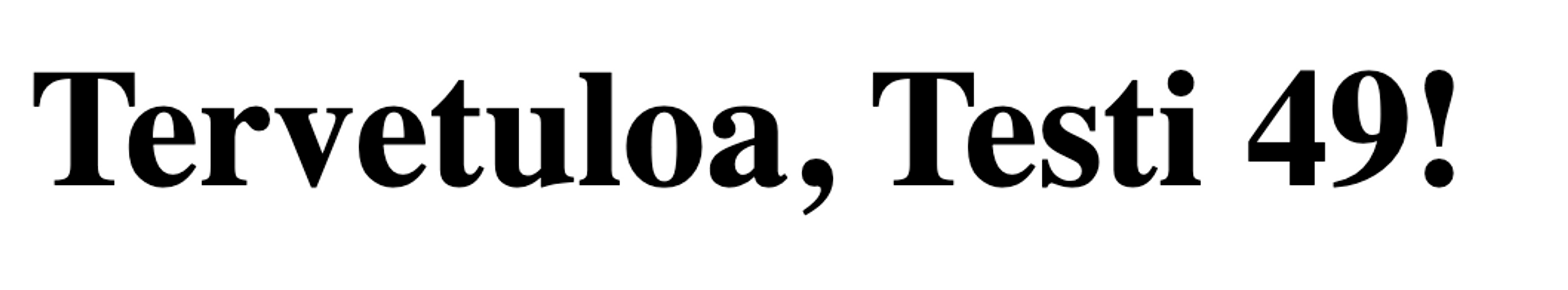
Exploiting Vulnerability
Template injections almost always result in an attacker being able to execute arbitrary code on the application server (RCE, Remote Code Execution). How the execution of the code is achieved varies quite a bit depending on the programming language and template engine. We will explore these in this course.
Template injection is easy to avoid. You just need to keep the template completely static, so that the template itself cannot be affected in any way. Only the data in the template can be influenced, not the structure.
All dynamically built templates are a danger zone.


Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



