What is OOXML?
OOXML (Office Open XML) is a file format developed by Microsoft for office documents, based on ZIP and XML. In practice, all Word and Excel files are therefore zipped XML, which means that OOXML processors may also be vulnerable to XML attacks, such as XXE.
Practical example
Start the exercise below and continue reading.
Model order
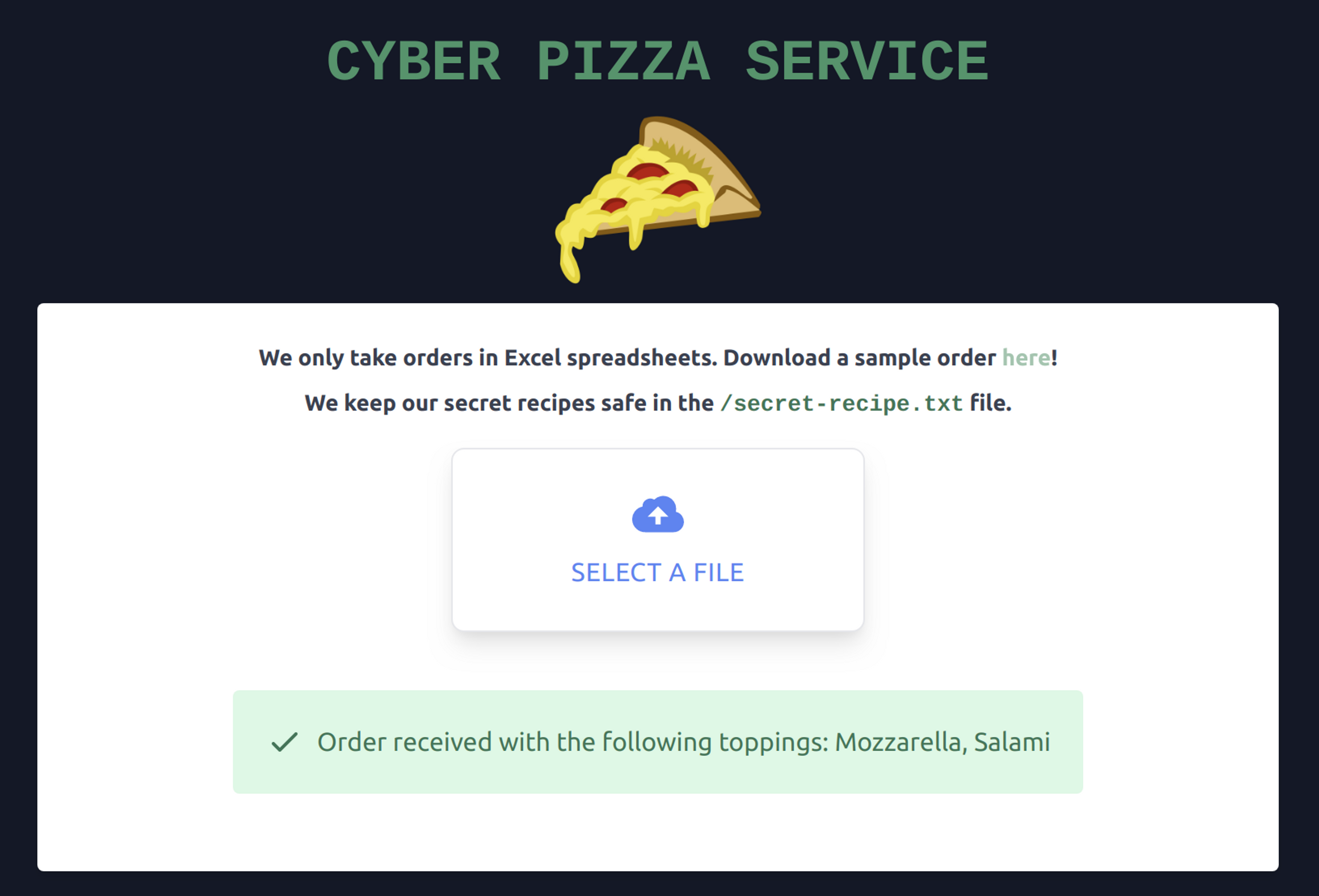
Download the sample order from the lab's address "/static/order.xlsx", open the attacker's code editor, and then drag and drop the file into the /root directory.
Terminal
Start the terminal by selecting the hamburger menu in the code editor -> terminal -> new terminal. Go to the /root directory if you are not already there.
cd /rootRun the ls command and you should see that "order.xlsx" is there.
see
CachedExtensions Machine User coder.json extensions logs machineid order.xlsx webExtract Excel
As already mentioned, Excel files are simply zipped XML files. Create a directory named "order" and use the unzip command to extract the file into the directory.
mkdir order
unzip order.xlsx -d order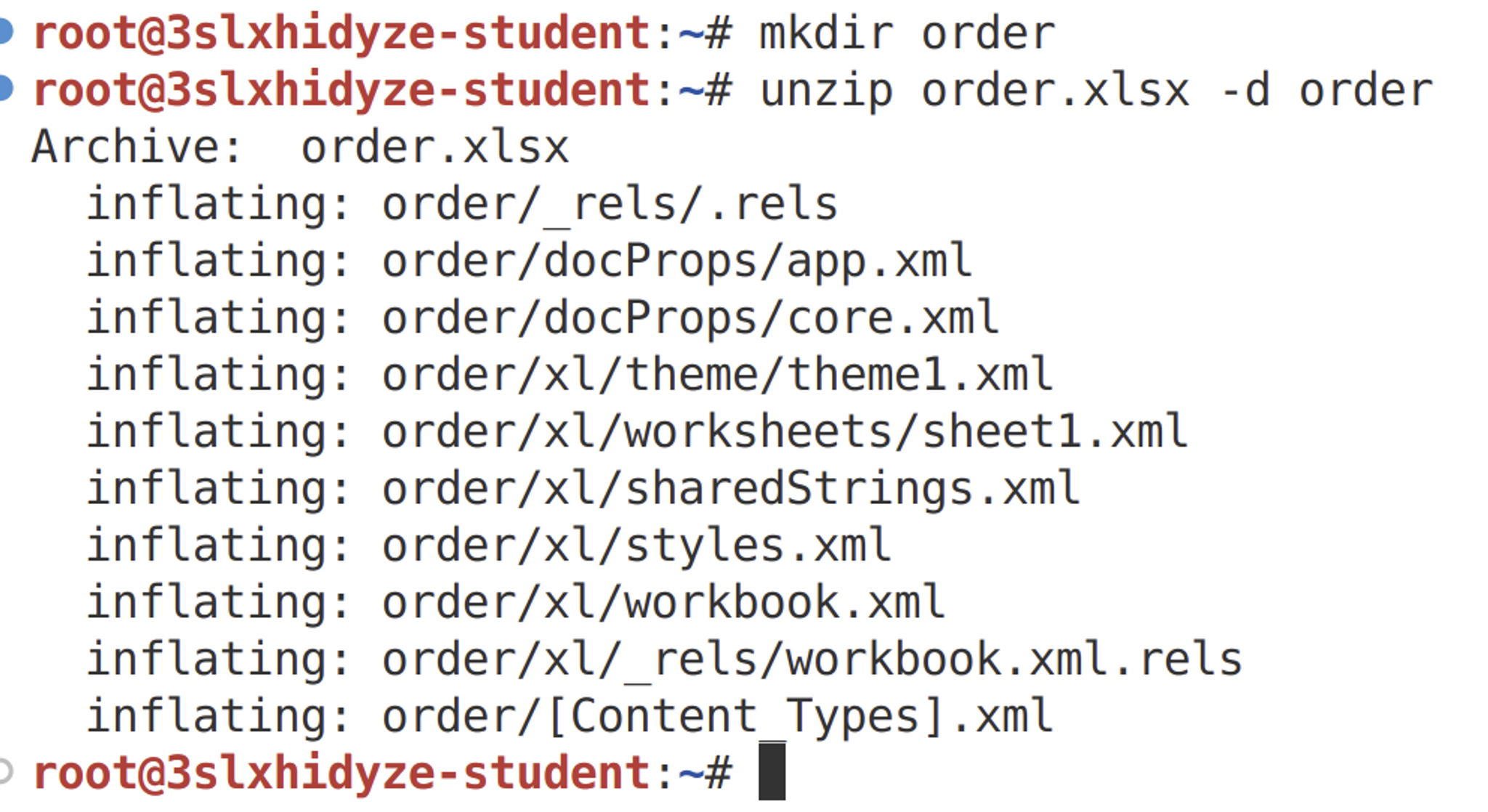
Repackaging script
Let's create a small shell script now that we can use to repack Excel. Right-click on the root directory, select "new file" and give it the name "repackage.sh". Enter the following text:
#!/bin/bash
(cd order && zip -r /root/evil.xlsx ./*)Grant execution rights to the script:
chmod +x ./repackage.shTest settings
Try that the repackaging script works.
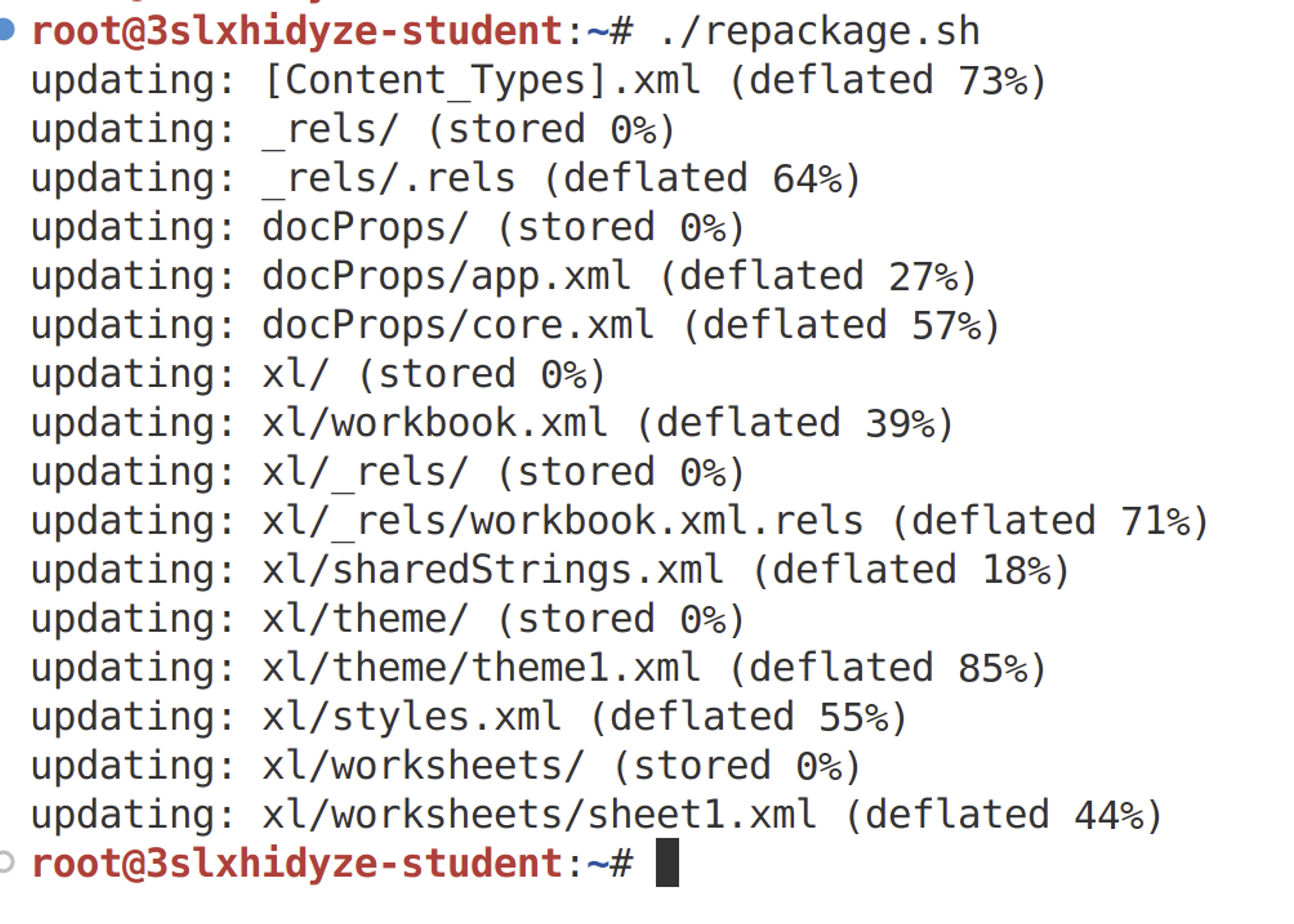
Then download the generated evil.xlsx file. You can do this by right-clicking on 'evil.xlsx' in the code editor and selecting "Download".
Return now to the pizza service, download the order, and confirm that the order works. Now we have a working foundation for building the attack.
Search location
In order to achieve reflected XXE, we need to determine where in the Excel file the words "Mozzarella" and "Salami" can be found. We can use the grep command to find this out.
grep -r Mozzarella ./order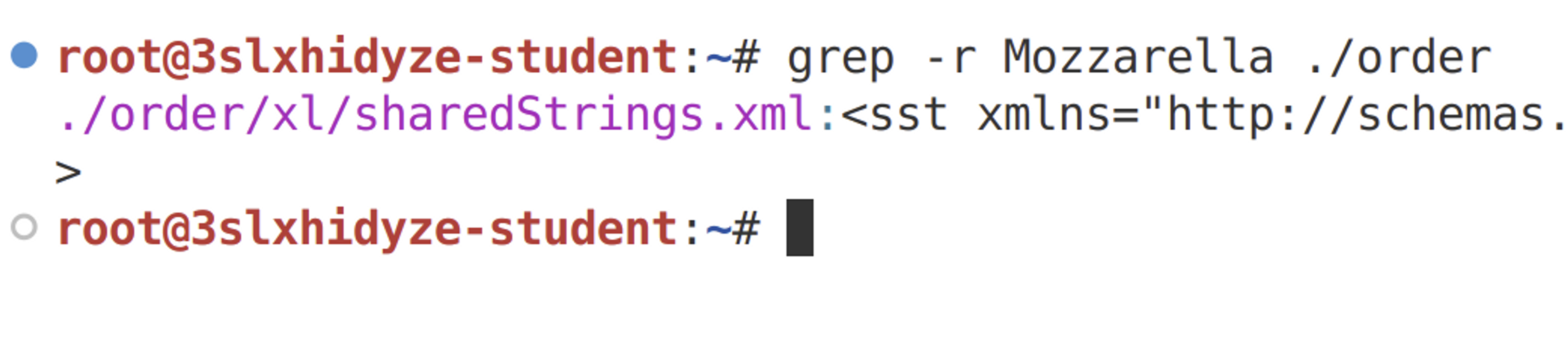
It seems that "order/xl/sharedStrings.xml" is the correct file. Open this file in the code editor.
XXE
By now, you should already know how to proceed from here. If this step doesn't feel familiar, go back to the previous modules in this course.
Create a DTD entity that points to the /secret-recipe.txt file, and then execute that entity instead of Mozzarella or Salami.
As a reminder, the syntax for DTD is:
<!DOCTYPE root [ ]>And the syntax of the external entity is:
<!ENTITY name SYSTEM "url or path">And the syntax for executing the entity is:
&name;

Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.



